by Muhammad Haekal Alghifary, Security Researcher @ ITSEC Asia
Let's face it, we use Sigma as Sigma provides a standard format that works across different platforms. Sigma acts like a universal language for detection rules - you write a rule once, and it can be translated to work in Elasticsearch, or other security tools. And we acknowledged, this solve a problem: Without Sigma, teams must rewrite the same detection logic over and over for each different system.
However, there was still a gap: even with Sigma rules, we still need an easier way to actually use them for threat hunting. We built a platform to bridge that gap - making it simple to use Sigma rules for efficient threat hunting.
Why this tools exist?
For us, Sigma is one of the cool concepts. It provides a standard, easy-to-read YAML format that let us share detection logic for specific threats, like a new ransomware strain or an attacker technique. So, let say you work for company A and use SIEM A, and me work form company B we use different SIEM, we still be able to share a detection rule that we both can actually use it.
But, even with a perfect Sigma rule, we still have a workflow that is still bumpy. Imagine you find a great rule for detecting Cobalt Strike, what happens next?
- Find a converter: You have to find and use
pySigmato manually convert the YAML rule - Copy-paste the converted query into your SIEM tools and set the time frame
- Run the search and wait for results
- Repeat 🔁 because you need to be thorough, you have to do this for ten more rules, one at a time
This process is slow and doesn't scale. Hunting for a complex threat could mean repeating these steps dozen times.
This is why, we built this tool to eliminate manual and repetitive work.
How to use this tools: Finding Cobalt Strike in Minutes
Scenario: You've just received intel that a threat actor is using Cobalt Strike. You need to quickly check your systems for any signs of an attack.
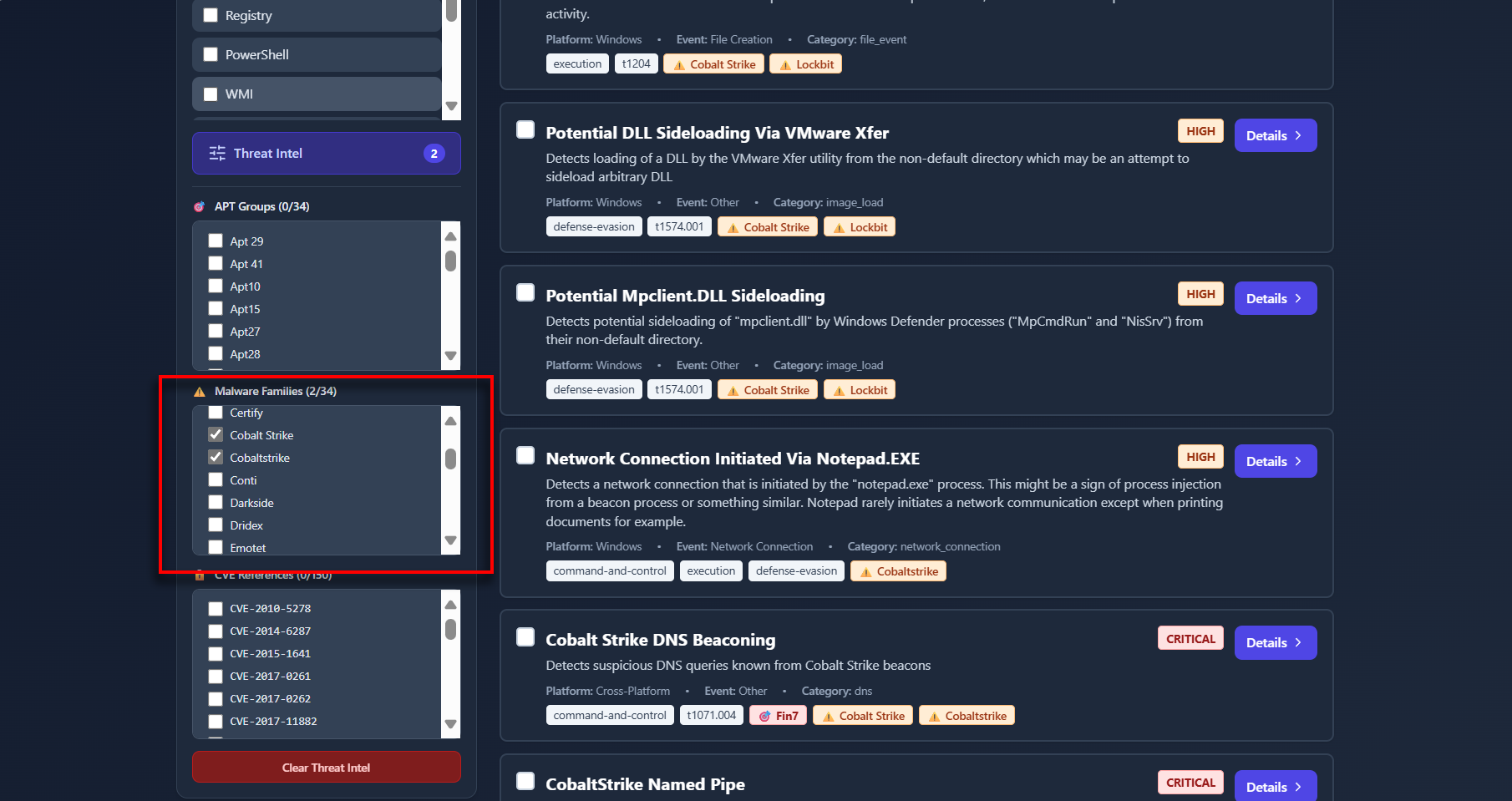
- Find the Rules: Instead of digging through articles, you just have to filters and select "Cobalt Strike".
- Focus the Hunt: To reduce noise, you filter for "Critical" and "High" severity alerts.
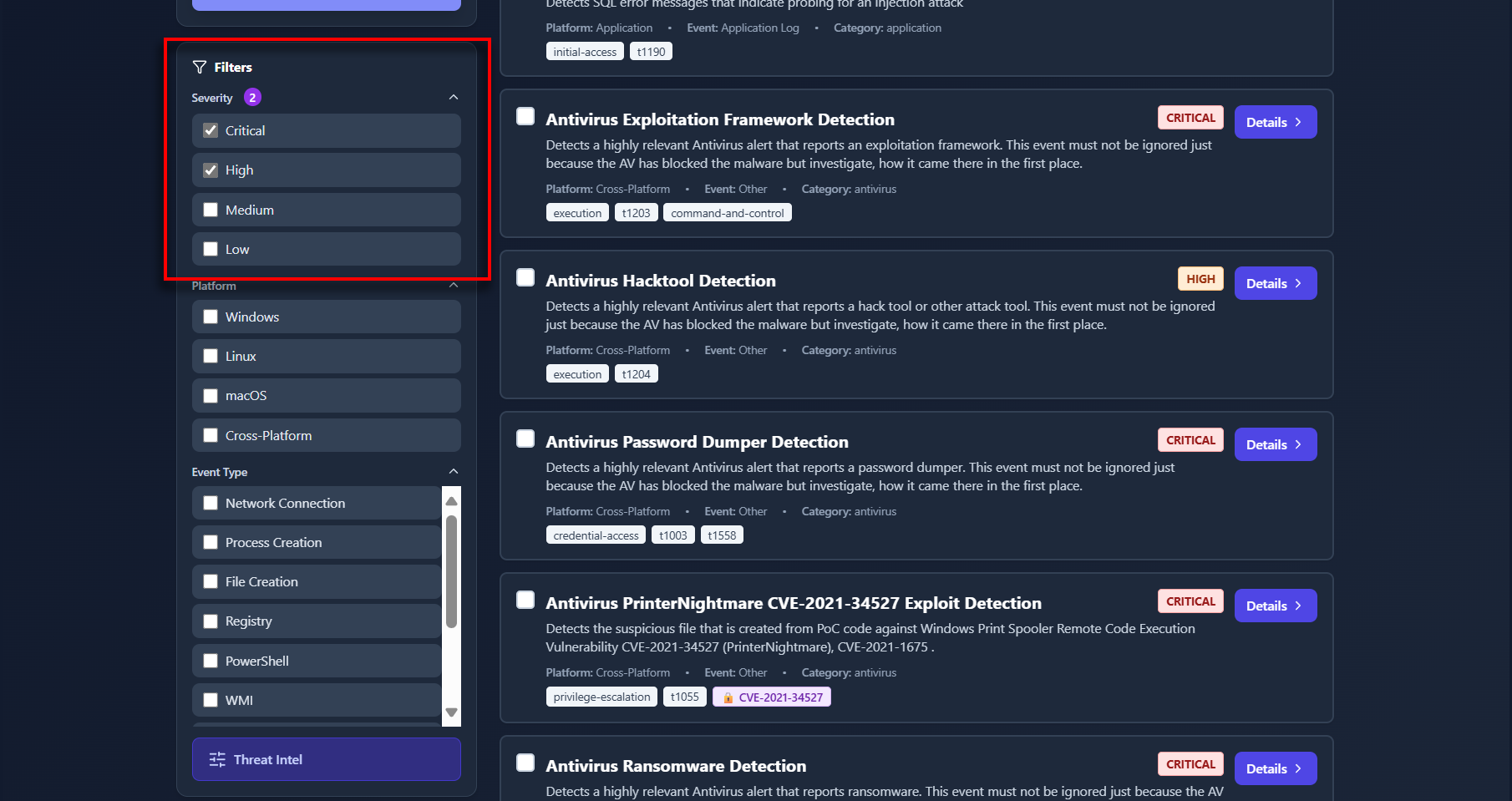
You’ve now narrowed down the total 3,528 rules to 39 high-fidelity rules. You can press the “Select All” checkbox to select all the filtered rules.
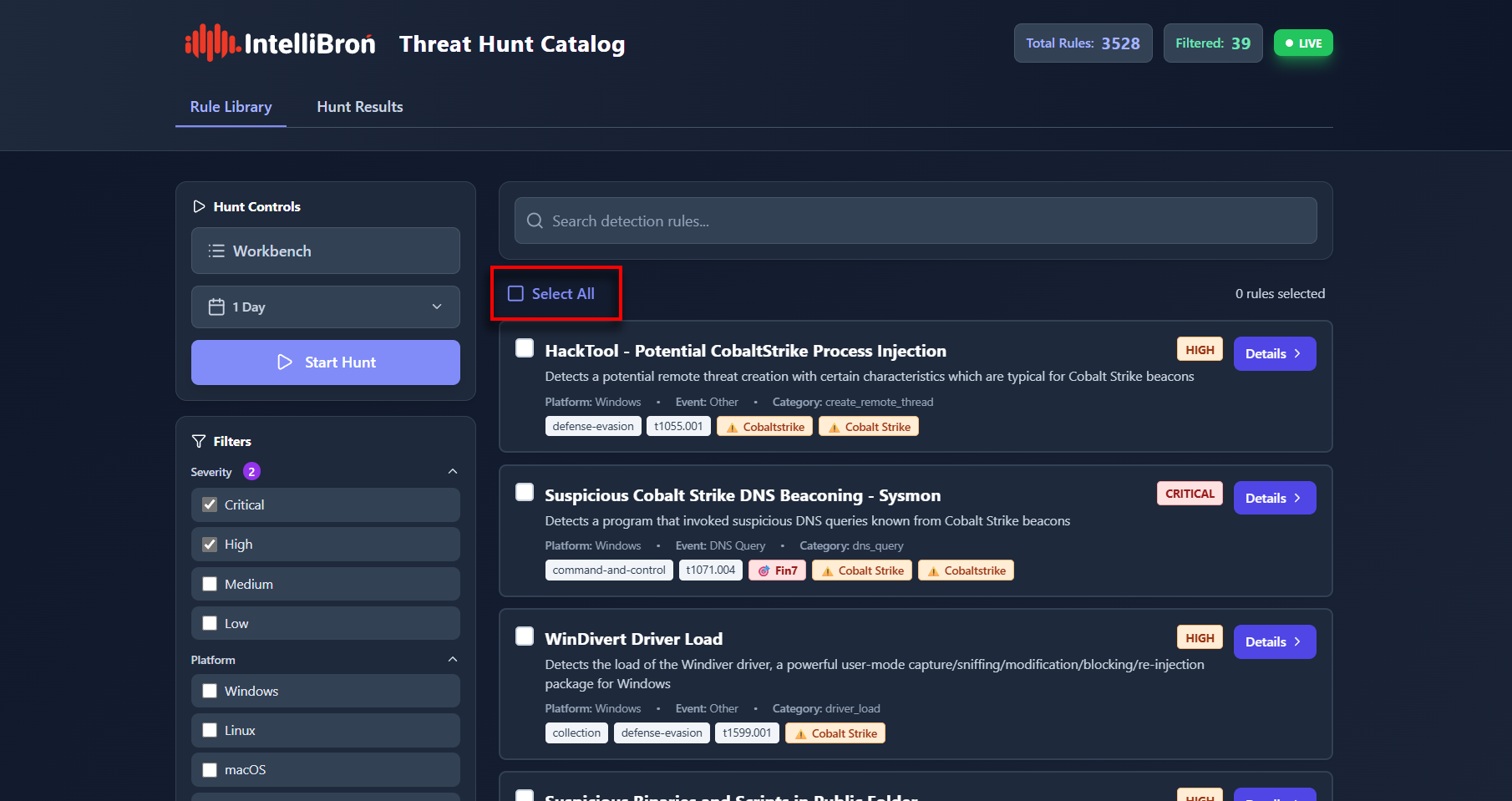
Once you click the checkbox, the selected rules are placed into a workbench, where you can further manage them if needed.
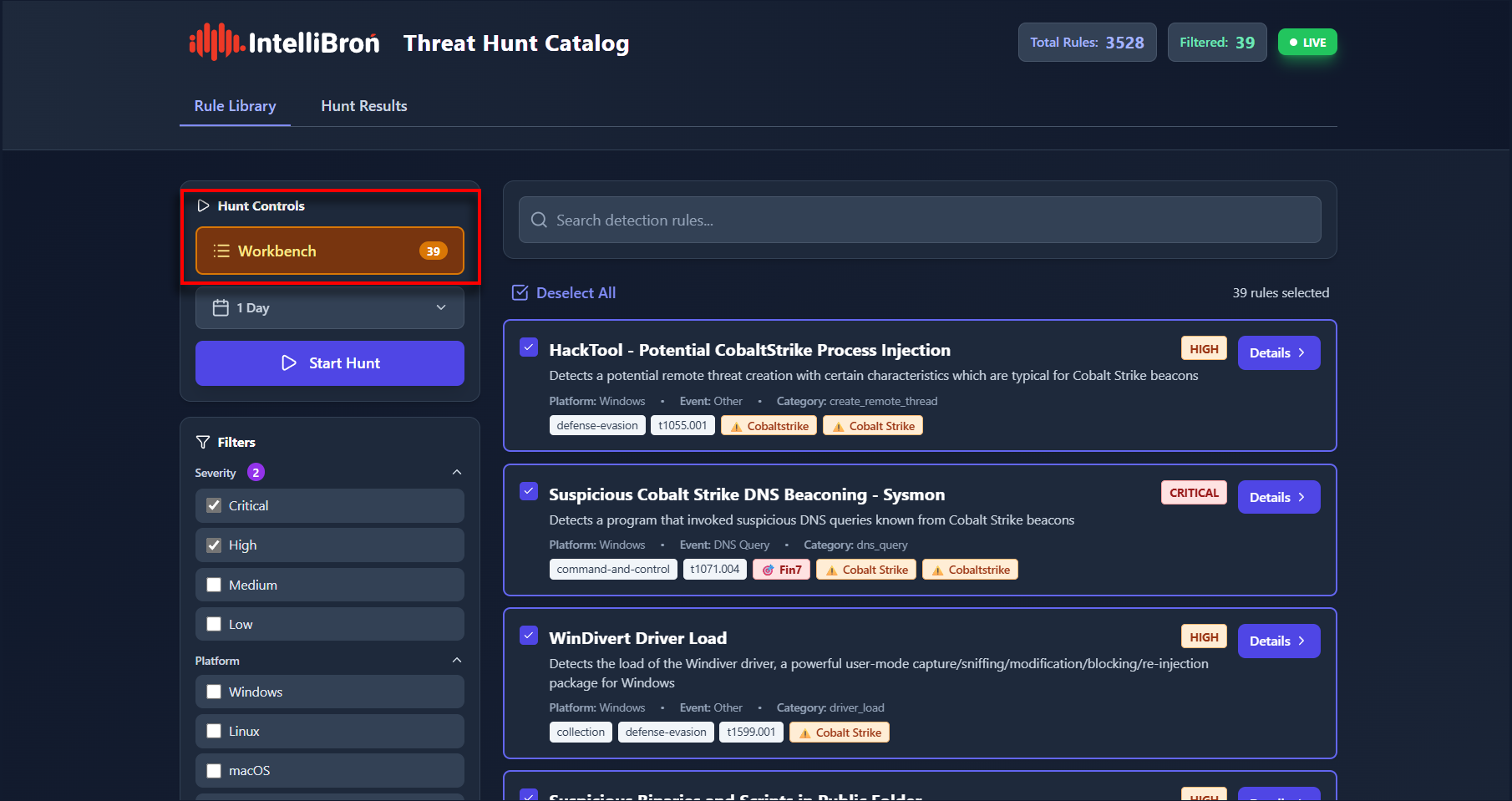
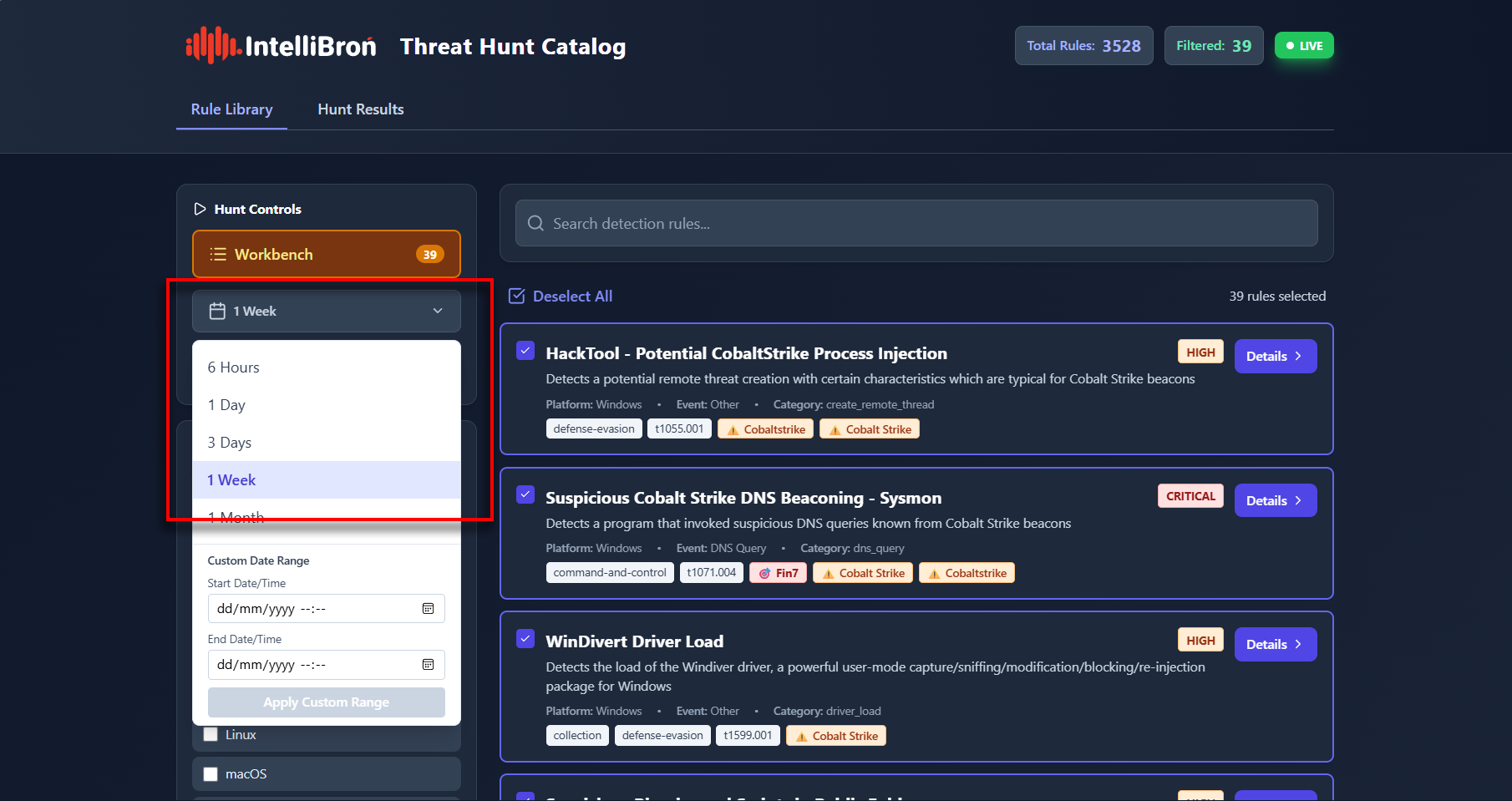
- Launch the Hunt: You can set the search window to the "Last 1 Week"
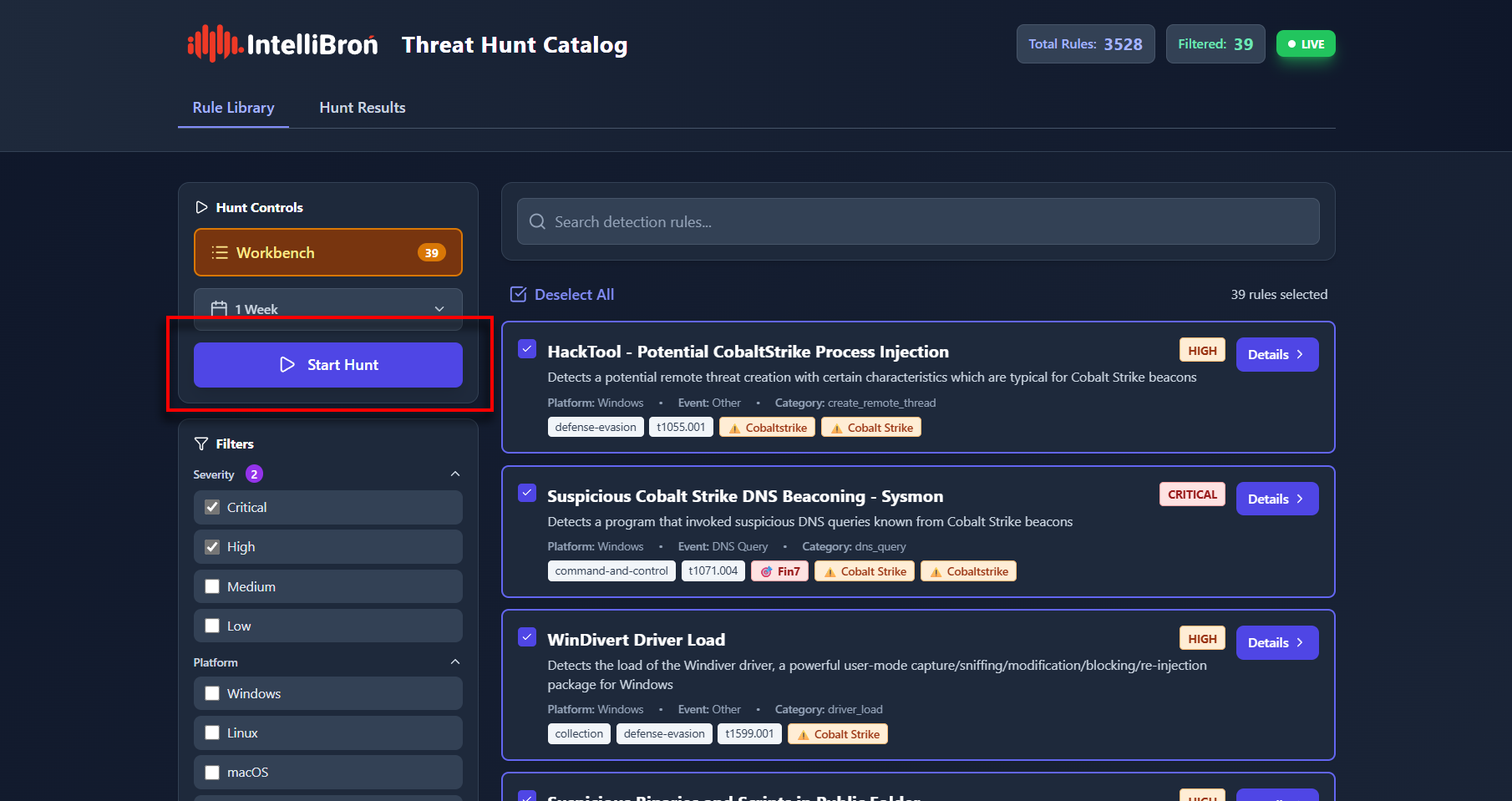
Once everything is configured, click the “Start Hunt” button to launch the query.
- Review the Findings: A couple of minutes later (depending on your connection and log size), the results are in.
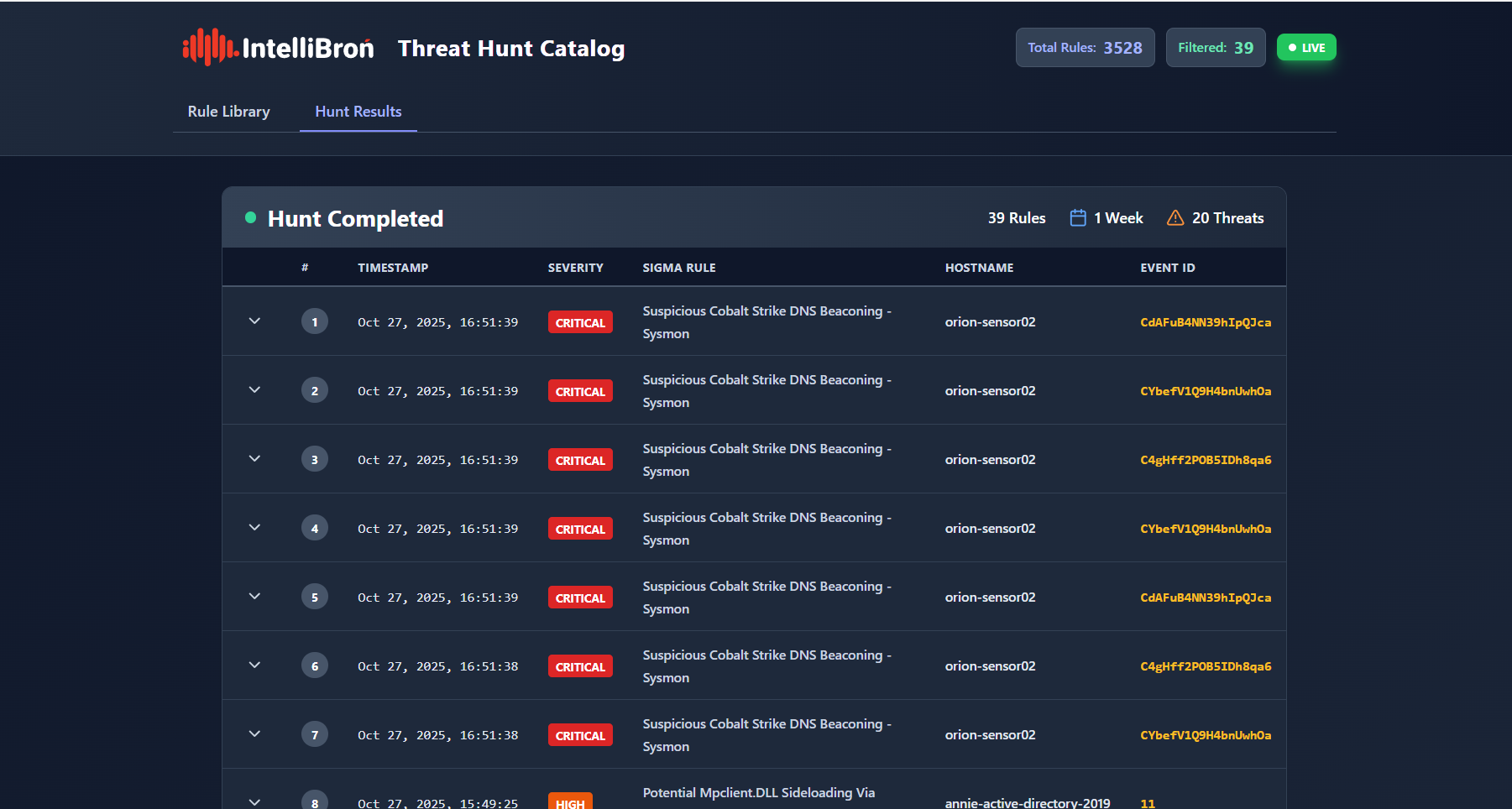
You have 20 results related to Cobalt Strike DNS beaconing and some Mpclient.dll sideloading rules. If you’re not familiar with a rule, simply click its title to navigate to the Rule Detail page.
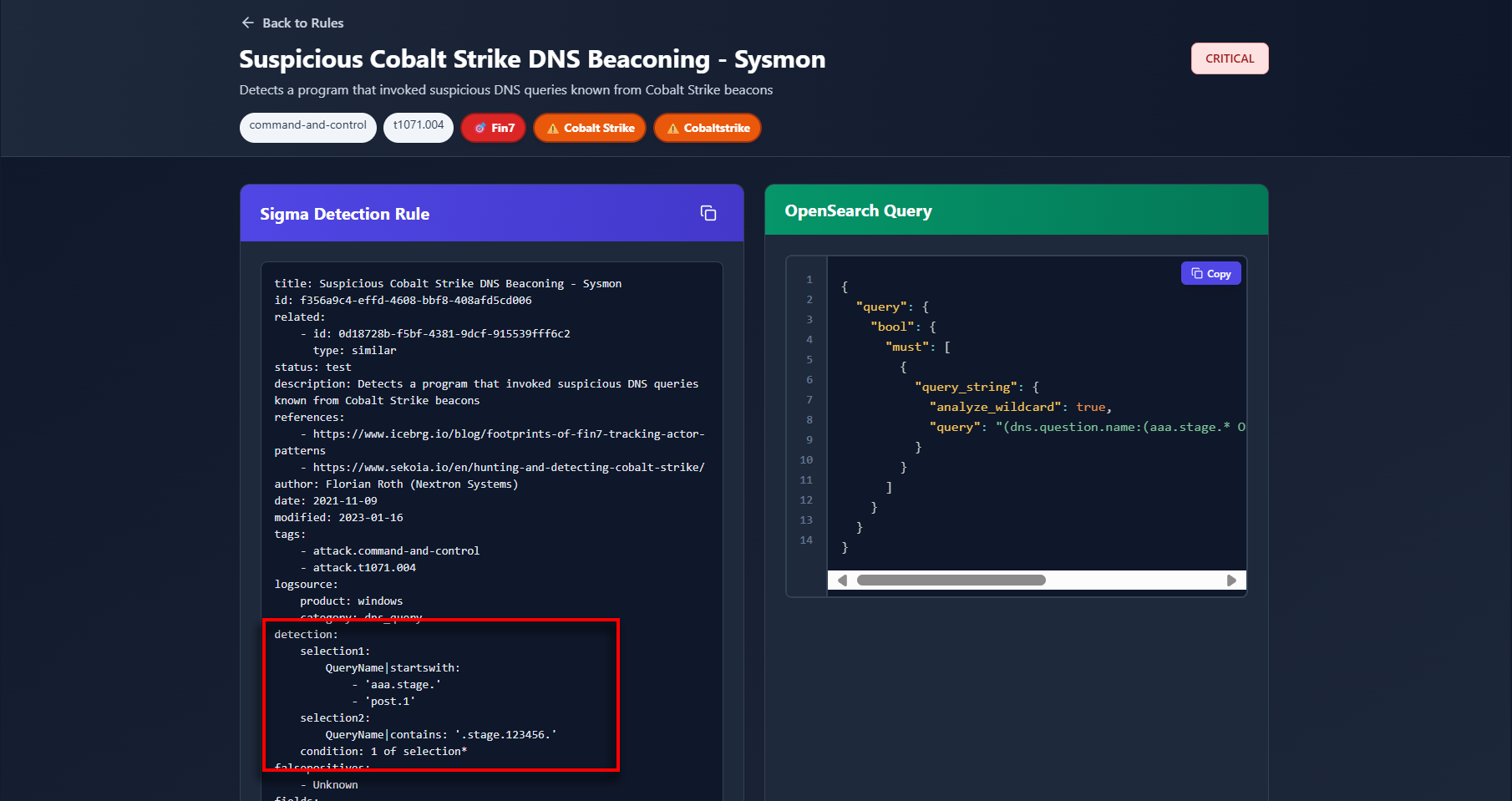
For example, the rule “Suspicious Cobalt Strike DNS Beaconing – Sysmon” detects DNS queries for domains starting with "aaa.stage.", "post.1", or containing ".stage.123456." anywhere in the domain name. On the right-hand panel, you can also view the converted Sigma to OpenSearch query.
- Investigate and Escalate: Expand the result to view the full event details and confirm it’s a strong indicator of compromise.
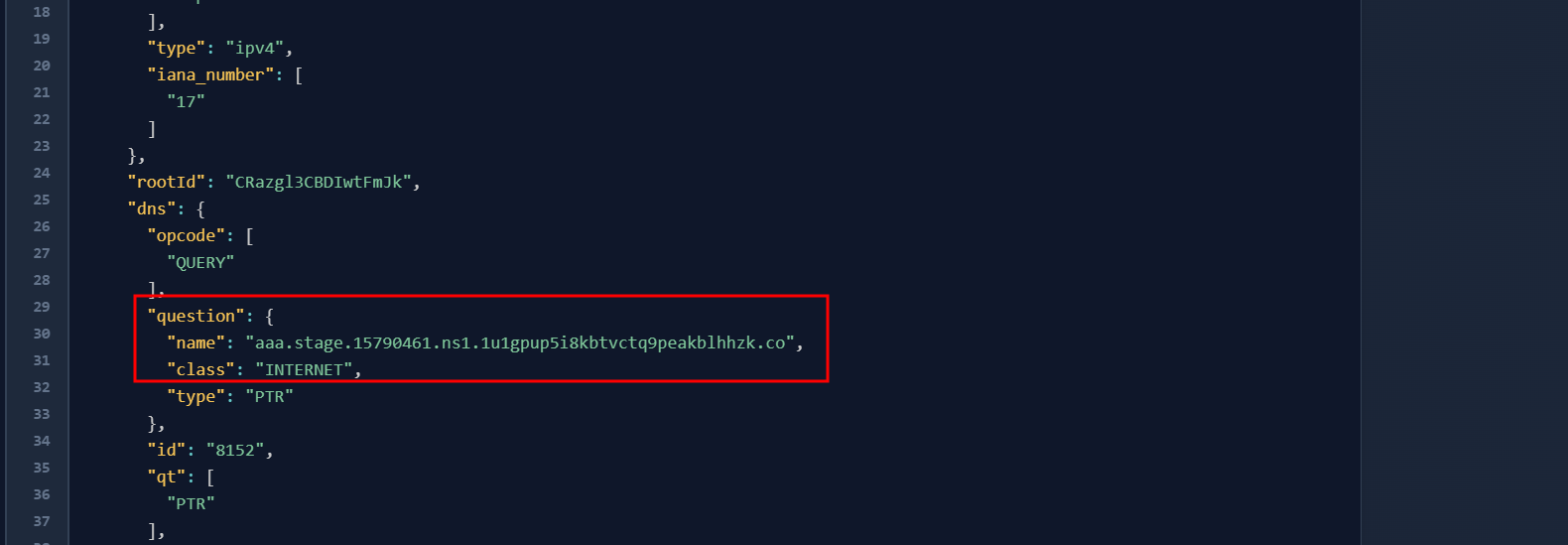
The result: In under five minutes, you went from threat intel to finding evidence of an attack.
Try it Now!
If you're interested in testing this platform, the source code is available on our GitHub repository. We welcome you to explore, test, and experiment with it in your environment.
This is an actively developed project, and we're constantly working to improve it. If you encounter bugs, or have a feature requests. Please:
- Open an issue on Github to report bugs or suggest features;
- Submit a pull request if you'd like to contribute code improvements.
Your feedback helps make this tool better for community.
Lastly,
We hope this platform helps you be fast and accurate by making Sigma easy to use every day. By handling tedious part of threat hunting so you and your team can focus on what humans do best: analysis and investigation.
By turning a library of rules into interactive hunting tool, we hope security operation can be more effective. You get your most valuable asset: time.
Thanks for checking this out. If you try it out, we'd genuinely love to hear about your experience. Happy hunting!




