Aplikasi Android pakai Jetpack Compose, jadi lebih aman?
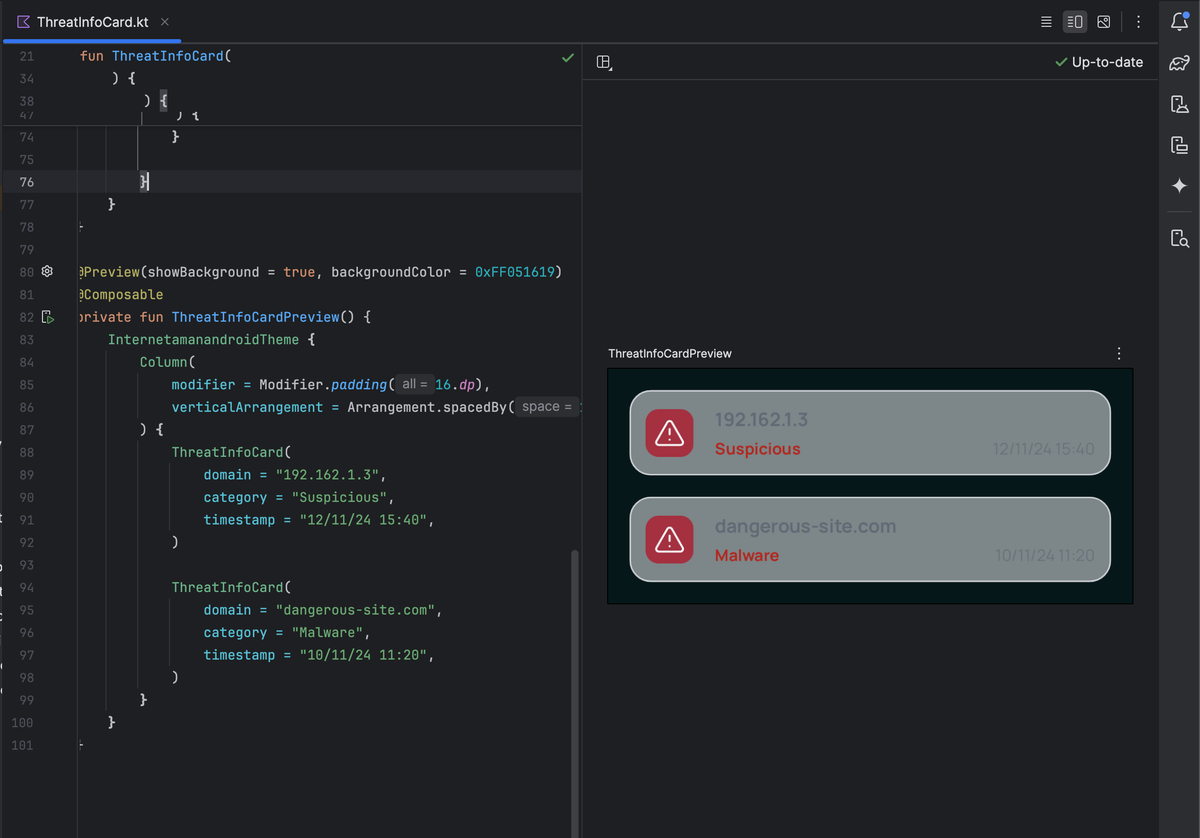
Jetpack Compose offers more than simplicity—it brings security through code obfuscation. Unlike XML layouts easily decompiled by hackers, Compose UI code gets scrambled by R8 with Kotlin functions, making your app's structure harder to reverse-engineer while boosting productivity.