1. The Global Scale and Impact of Stealer Malware
1.1. Breaking In Without ‘Breaking’ Anything
What if we told you that breaking into a system today often requires no complex exploits at all?
Despite years of headlines and hacker movie stereotypes, hacking is still commonly associated with techniques like SQL injection, code execution, privilege escalation, and other attacks that sound sophisticated and hard to pull off.
But in reality, many breaches begin far more simply. No exploits. No fancy payloads. No need to break in. The attacker just walks through the front door with stolen credentials.
And this isn’t just an anecdote, it’s backed by data. The 2025 Verizon Data Breach Investigations Report (DBIR) found that 32% of all breaches involved stolen credentials.
So where does this massive supply of credentials come from?
Technically, they’re the product of a well-oiled underground economy where data is systematically harvested, traded, and reused. In recent years, the primary engine of this ecosystem has been stealer malware: a lightweight, evasive programs designed to silently extract browser-stored passwords, session cookies, crypto wallets, and other sensitive data from infected machines.
This vast collection of harvested credentials then becomes a valuable commodity for threat actors to trade and exploit. But its impact goes far beyond simple account takeovers. For cybercriminals, it often serves as the gateway for more destructive attacks like ransomware. In fact, the same Verizon report shows that 54% of ransomware victim domains also appeared in stealer logs, underscoring how stealer malware often lays the groundwork for broader compromises.
This connection to ransomware underscores the urgency of understanding just how widespread this problem really is.
1.2. The Global Battlefield of Stealer Malware
On a global scale, what began as a quiet trend has grown into a full-scale epidemic. Fueled by stealer malware, an underground network of trade has spread across continents, infecting devices in waves and silently harvesting sensitive data from unsuspecting victims.
To grasp the true scale of this silent crisis, we analyzed tens of thousands of stealer malware incidents recorded between January and June 2025. The numbers aren’t spread out evenly. Some countries are seeing far more infections than others, pointing to how exposure and risk can vary widely across regions.

From a global perspective, we can see that several Asian countries feature prominently among the most affected. While it’s too early to draw definitive conclusions about regional risk, the presence of five Asian nations in the top ten collectively accounting for over 60% of observed cases, suggests that the region is facing disproportionately high levels of exposure to stealer malware.
Here’s how the numbers stack up across the top ten most affected countries in Asia:
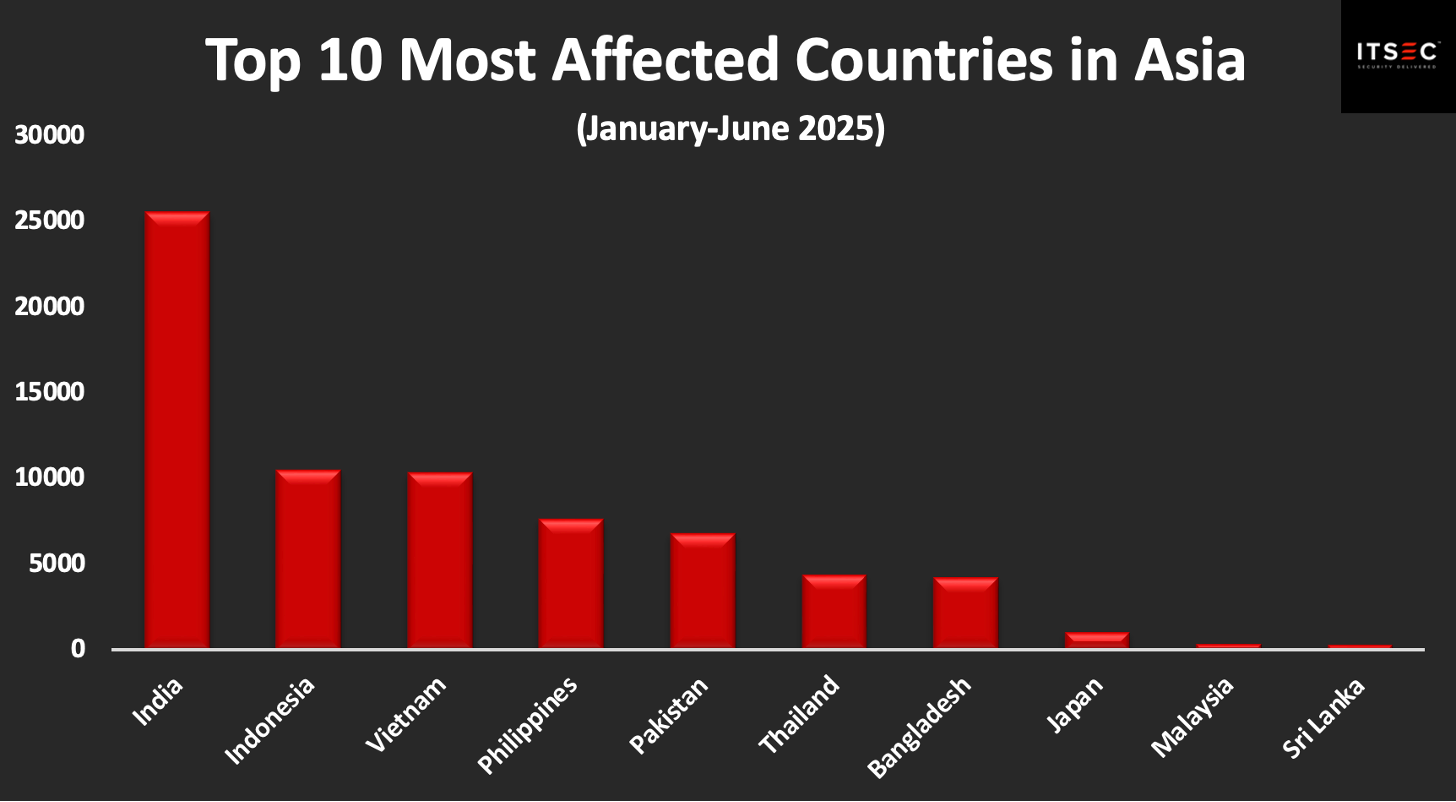
Looking at this region alone, the infection landscape reveals an even more concentrated pattern. India alone accounts for more than a third (35.70%) of all stealer malware incidents in the region. Following closely behind are Indonesia (14.72%) and Vietnam (14.50%), with the Philippines and Pakistan also contributing significantly.
With infection numbers this high, the real question isn’t just about scale, it’s about substance. What exactly is being taken, and how? To get a clearer picture of the impact, we need to look beyond the percentages and examine the harvested data from these attacks: stealer logs, which consist of bundles of stolen credentials, session cookies, and other sensitive data.
2. Anatomy of a Stealer Operation
2.1. What are Stealer Logs?
So, when a device is successfully compromised by stealer malware, what actually gets taken? The answer often lies in the stealer log. This “log” isn’t just a single stolen password, it’s a partial snapshot of a victim’s digital life, neatly organized and either published for free or sold on the black market.
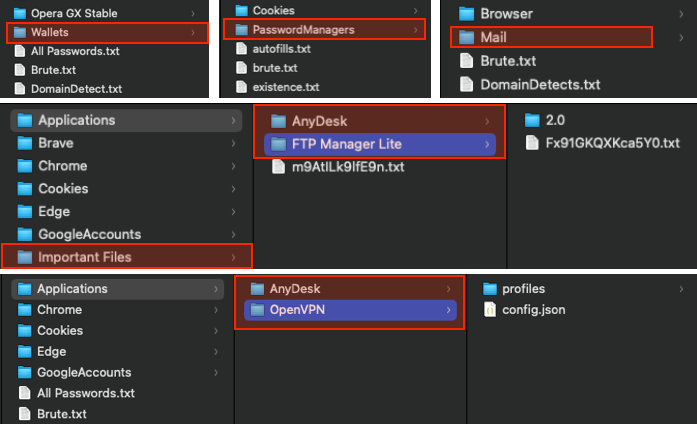
What makes these logs particularly dangerous is how complete and convenient they are. Instead of sifting through raw dumps or scattered credentials, threat actors receive a curated bundle: browser-saved passwords, session cookies, autofill entries, and configuration files from apps like VPN clients, password managers, or crypto wallets. Many are tagged with machine and location identifiers, then neatly organized into folders named after the compromised device.
For criminals, this is turnkey access. And for defenders, it is a “forensic” snapshot that offers a view of what the attacker likely saw, touched, and potentially used.
2.2. How Are Stealer Logs Created?
A stealer log doesn’t appear out of thin air. It begins with the successful execution of stealer malware on a device, often triggered by the victim themselves.
In many cases, the infection begins with risky behavior such as downloading cracked software, using cheats for online games, running fake installers, or interacting with explicit or gambling content. These are common delivery channels, where the stealer is bundled with a legitimate-looking file or hidden behind an enticing download button. Once the file is executed, the stealer runs silently in the background.
However, not all infections rely on user intent. Social engineering tactics such as phishing emails or fake updates delivered through compromised websites are also widely used. In more targeted scenarios, attackers may exploit system vulnerabilities or weak credentials to gain access and deploy the stealer manually, without requiring any user interaction.
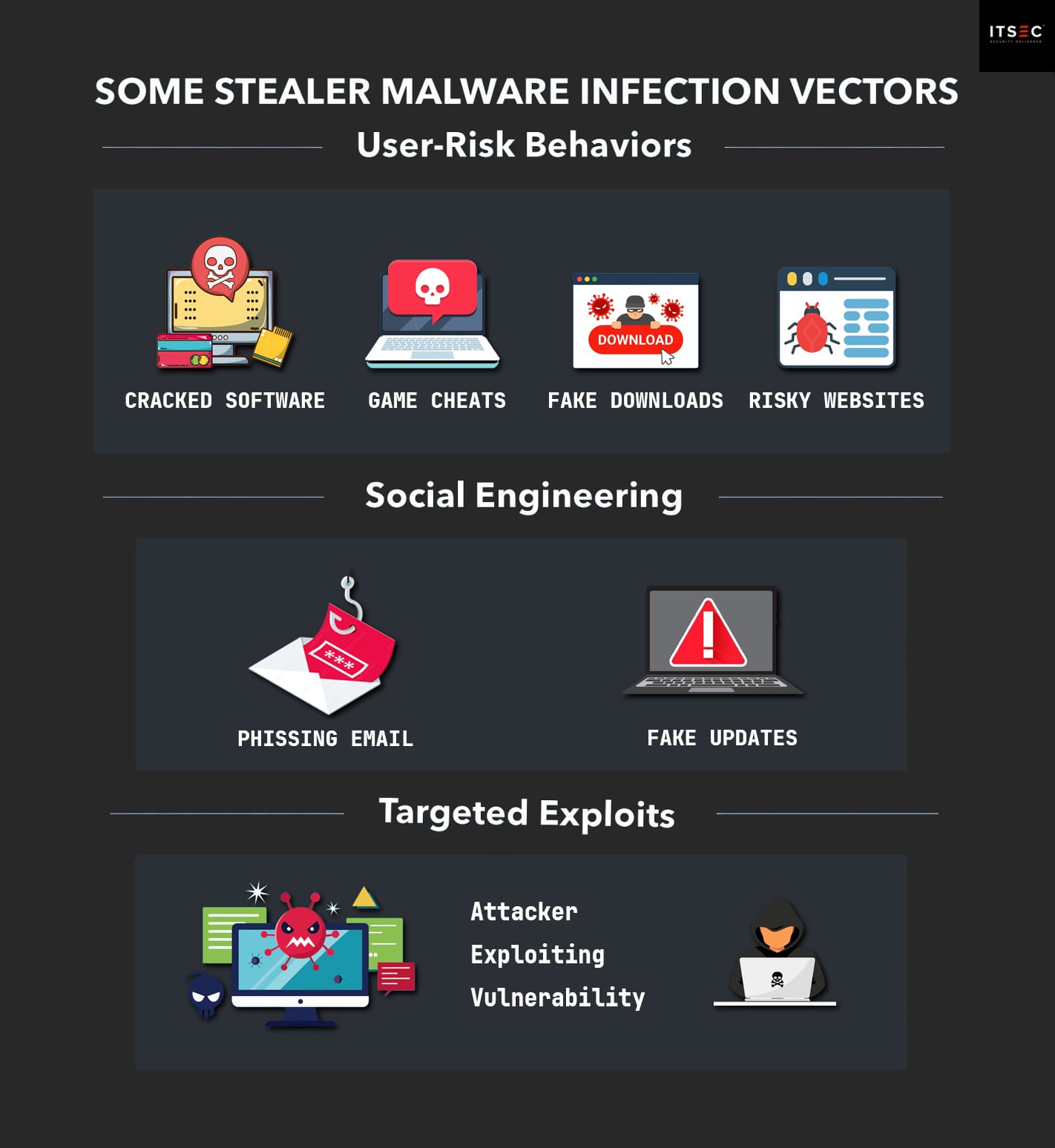
Regardless of the infection method, once the malware is active, it immediately begins the harvesting process. It scans specific file paths, browser databases, and application folders to collect a wide range of sensitive data. This data is typically compressed into a structured archive and may be encrypted before being sent to the attacker’s control host or uploaded to a file hosting service.
From infection to exfiltration, the process often takes less than a minute. And when it’s done, there’s usually no visible trace for the victim. Just a neatly packaged log, now circulating in the underground economy.
2.3. What Do These Logs Typically Contain?
As mentioned, a stealer log is a collection of digital information, structured for optimum efficiency. While capabilities vary between malware families, most logs contain a core set of data harvested from the most common sources on a device.
Chief among these sources is the web browser, a central hub for digital identity. Stealer malware systematically extracts a broad range of sensitive data, including saved usernames and passwords, complete browsing history, session cookies that may, in some cases, allow access to authenticated services, and autofill records that often contain full names, physical addresses, and payment card details.
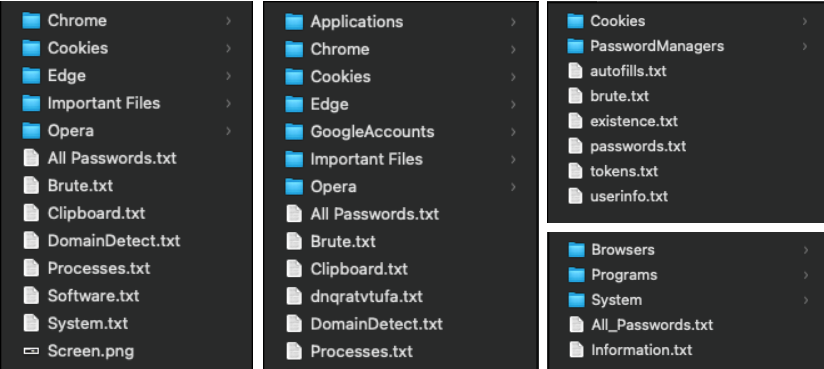
But the harvesting doesn’t stop at the browser. The stealer typically expands its reach by conducting a reconnaissance of the device itself, aiming to build a comprehensive victim profile. It compiles a detailed “system fingerprint,” which includes general device and user information like the computer name, hardware ID, OS version, installed software, IP address, and geographical location.
While this reconnaissance provides valuable context, the capabilities of many modern stealers extend far beyond it. Many stealers are built to pursue even more valuable targets, namely specific applications that hold the keys to a user’s digital assets or corporate access. These are not random grabs, they are targeted hunts for data stored in high-value applications used for authentication, remote connectivity, or financial management. The primary targets include:
- Credential vaults from Password Managers, configuration files from FTP Clients, and sensitive data within Email Clients.
- Session tokens and configuration files from VPN applications, often used to replicate a user's access into corporate networks.
- Local Cryptocurrency Wallet files, such as wallet.dat, and exposed private keys that enable direct asset theft.
2.4. The Heart of the Log: passwords.txt and Friends
From this vast collection of stolen data, one file consistently stands out as the crown jewel in nearly every stealer log: passwords.txt. This file, often named passwords.txt, all-passwords.txt, or a similar variant, is arguably the single most valuable artifact for both attackers and defenders.
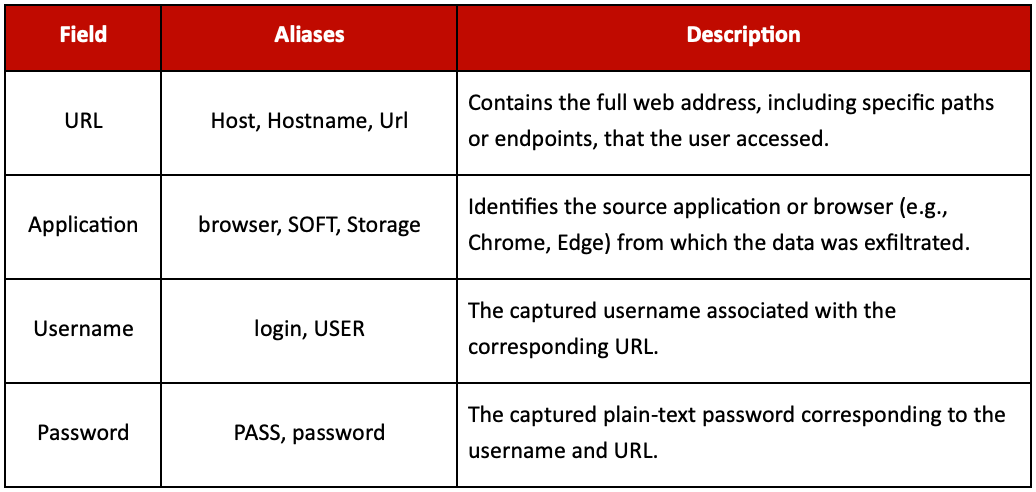
What makes it fundamental isn’t just its content, but its structured, immediately usable format. Unlike cookies or system files that may require further interpretation, passwords.txt delivers the most sought-after raw data in a clear layout:
- The originating URL or domain
- The username
- The password itself
- The application or browser where the credential was stored
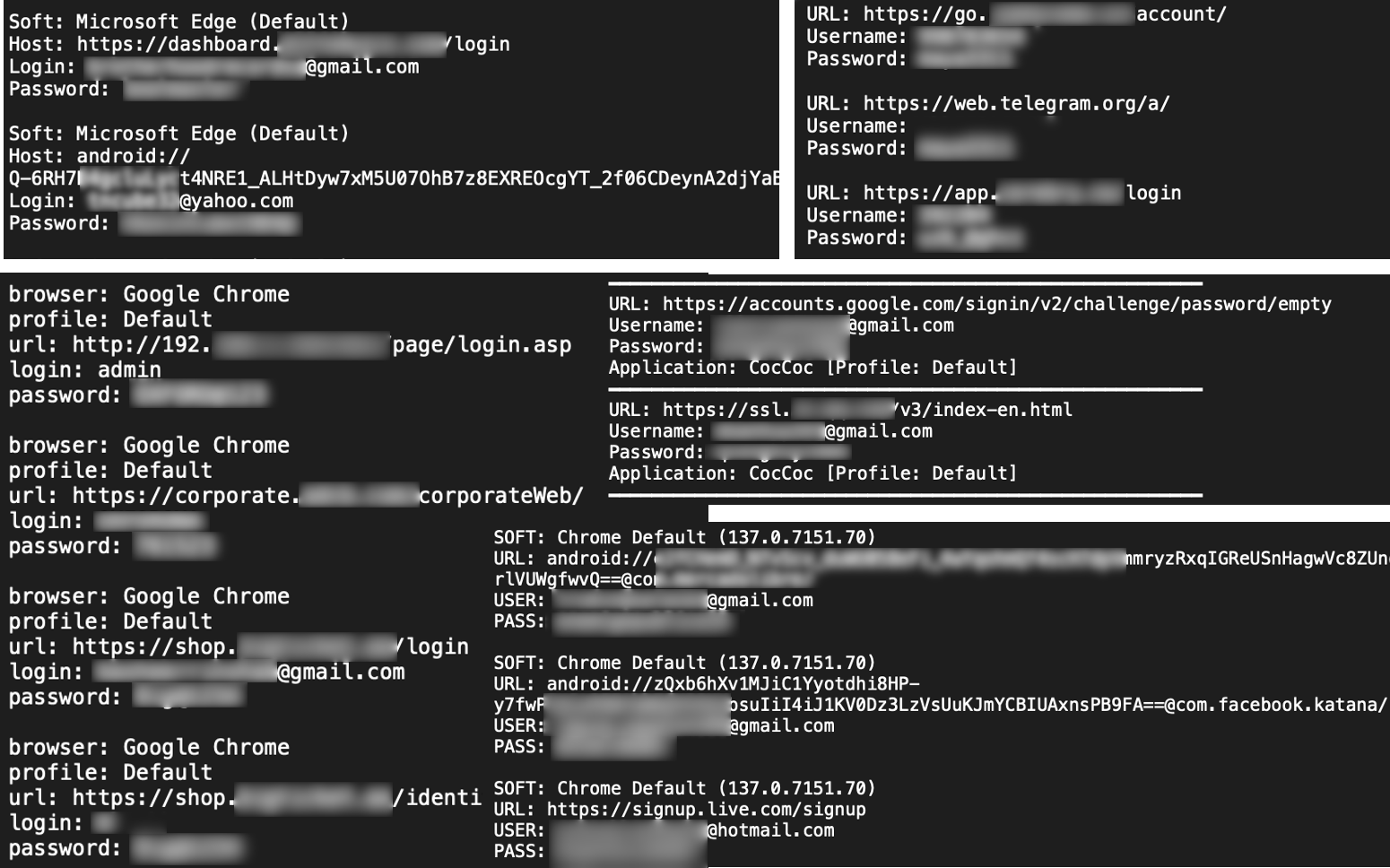
This “ready-to-use” nature makes passwords.txt the most efficient starting point for analysis. Its presence and quality often serve as the primary factors for an analyst to determine whether a log is high-value or not. Ultimately, this file itself is the 'stolen key' that enables a new class of attacks.
This new reality, where attackers can often bypass the hunt for vulnerabilities entirely by simply using stolen keys, has profound implications for how we approach security.
This raises a critical question, “If attackers have such a powerful tool at their disposal, how can security professionals, on both the offensive and defensive sides, leverage this same "attacker's-eye view" for their own purposes?” The answer lies in understanding the practical applications of these logs in modern security testing and incident response.
3. Leveraging Stealer Logs for Attack and Defense
The existence of stealer logs has reshaped not only how attacks unfold but also how security professionals can anticipate, replicate, and defend against them. These logs offer more than just a list of stolen assets, they provide a rare glimpse into how attackers operate, and more importantly, what they now expect to find.
From an offensive perspective, stealer logs have quietly become an unconventional shortcut into hardened environments. In scenarios where the front door remains locked, where login pages are reduced to minimal functionality, and brute-force entry seems futile, data from a stealer log can serve as a skeleton key, granting access not just to accounts, but to deeper layers of the system, often bypassing traditional exploitation entirely.
On the other hand, for defenders, the appearance of a stealer log should ring louder alarm bells than most common alerts. It doesn’t just indicate a potential compromise, it suggests an actual exfiltration has already occurred, and the attacker may have interacted with or replicated an active login using stolen session data. Recognizing this requires defenders to move beyond just cleaning the infected endpoint, it demands a forensic mindset and a re-evaluation of trust across affected systems.
So in this chapter, we will explore how both offensive operators and defenders are beginning to adapt to this stealer-fueled reality, and why understanding these logs may become essential for both attack simulation and incident response.
3.1. Stealer Logs in Offensive Ops: Walking through the Front Door
In real-world engagements, we know that not every target is misconfigured or wide open. Many enterprise applications expose only a minimal attack surface, a single login form, no public APIs, no debug paths in sight. These are what we often refer to as “hardened fronts,” where the initial stages of testing become a familiar cycle of dead ends. Hours are spent crawling for endpoints, brute-forcing logins, and injecting every imaginable parameter, all yielding no results. Even deep reconnaissance across collaboration tools like GitHub or Atlassian can come up empty.
This repeated failure often forces a shift in strategy. At some point, rather than pushing harder, we can start looking for the doorkey hidden somewhere else entirely, often found in stealer logs.
This shift in mindset mirrors the operational reality of many advanced threat groups. Take, for example, the APT group Dark Pink. As documented in industry reports, their operations targeting government and military entities across Southeast Asia, including Indonesia, Malaysia, and the Philippines, often begin not with exploiting a software vulnerability, but with carefully crafted spear-phishing emails designed to capture login credentials. By luring victims into entering their passwords on fake portals, Dark Pink gains the “keys to the kingdom” without ever breaching a single line of code.
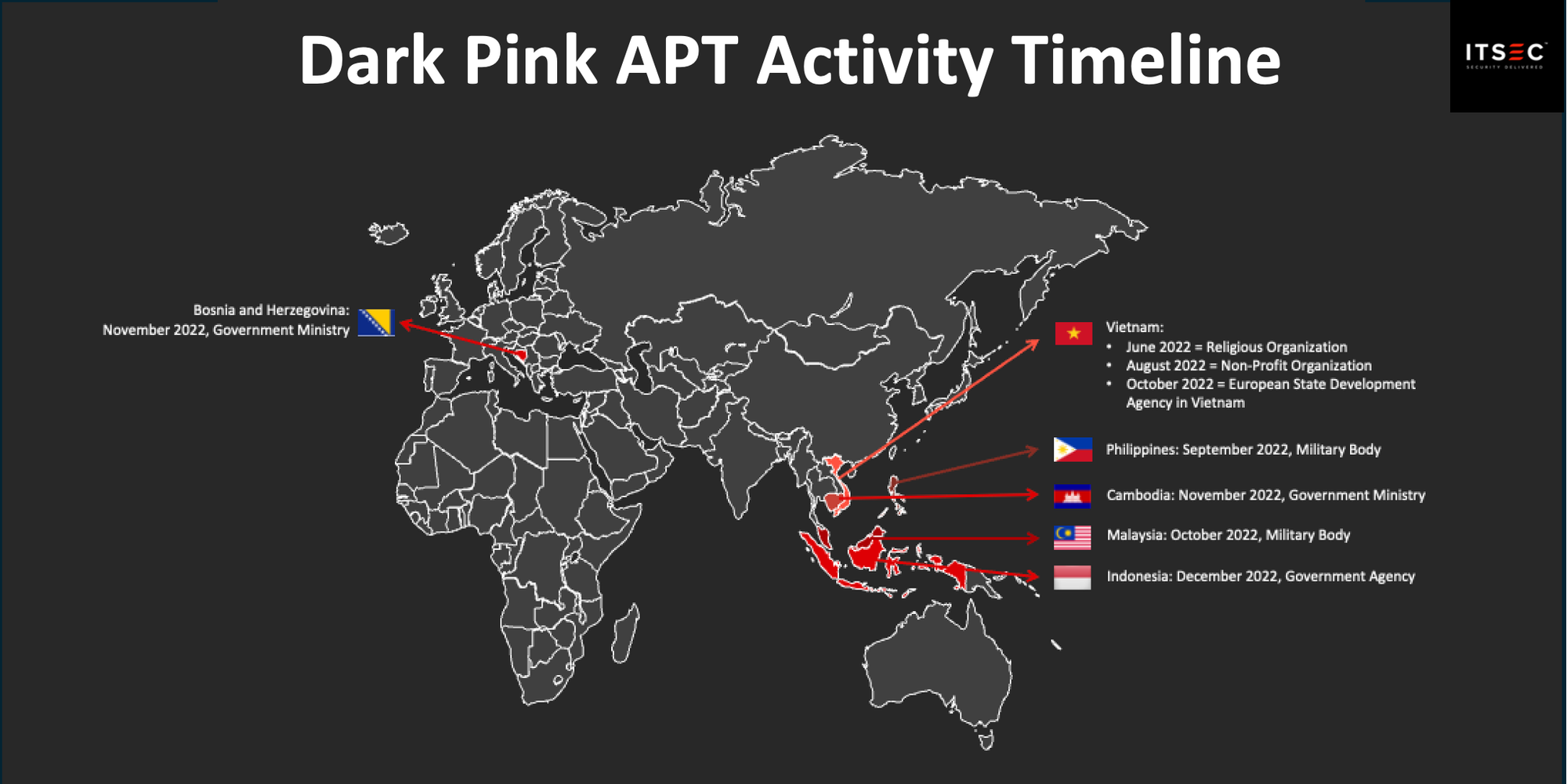
While their credential theft technique differs from stealer malware, the principle is the same, valid credentials unlock more than just access. The difference is that stealer logs scale this tactic passively, collecting credentials in bulk as victims unknowingly execute malicious loaders or cracked software bundled with stealer malware.
But how does this threat play out in day-to-day corporate environments and offensive engagements? The principles remain the same, but the opportunities often arise from more common, everyday situations.
Field Note I: The Leaky Browser Profile
In one real-world investigation, we encountered an employee who had synced their corporate browser profile on a shared home PC, used by their spouse and children. While gaming, the child installed cheat tools laced with stealer malware. This led to the compromise of not just the child’s credentials, but also the parent’s, including their corporate SSO account.
What began as a child downloading a game cheat on a family computer had now escalated into a direct threat to the corporate network, all due to a single, leaky browser profile.
This case perfectly illustrates how the modern attack surface reaches deep into personal territory, and why the corporate security boundary no longer stops at the office firewall. The real weakness wasn’t in the code, but in a policy that let a trusted identity bleed into an untrusted environment. For an attacker, exploiting these kinds of policy gaps and human behaviors is often far more effective than searching for a traditional software flaw.
Field Note II: How Stealer Logs Turned UUID-Based Access Control into a Flaw
In another case, we discovered a broken access control issue where user data was protected solely by UUIDs embedded in the URL. However, this created a classic dilemma: while the vulnerability clearly existed, it seemed practically unexploitable since UUIDs are random, non-sequential, and hard to guess.
However, that changed. When we analyzed a large set of stealer logs, we found multiple victims who had used this application. By reviewing their URL history, we harvested a substantial number of valid UUIDs, effectively turning a theoretical issue into a working exploit path. No passwords, no session hijacking. Just raw URLs leading straight to private data.
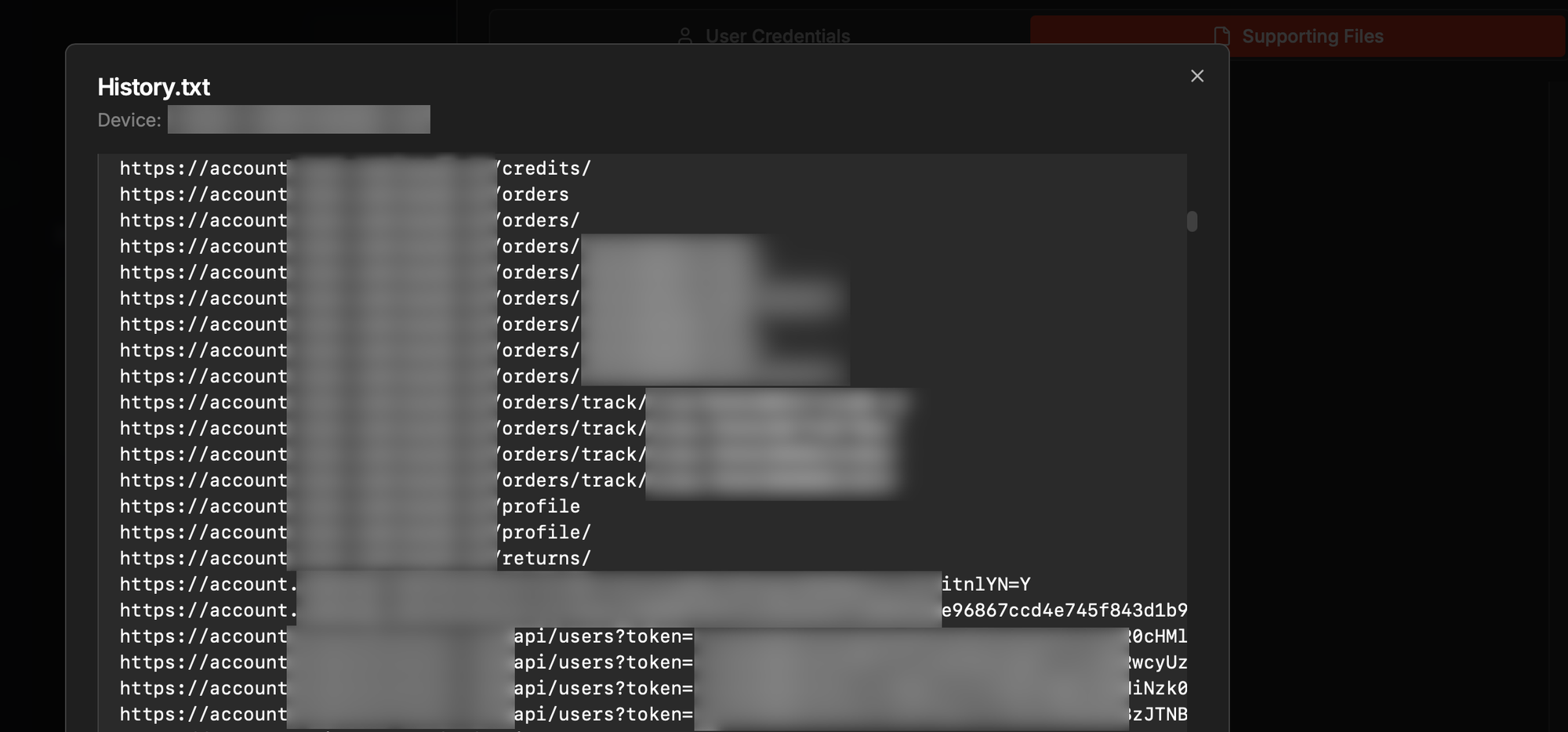
A reasonable question might be, “If the logs contain passwords, why bother exploiting broken access control?” In some cases, that’s a valid point. However, the application in question supported multiple login methods, namely users could either log in with a username and password, or use a passwordless flow by providing their phone number and receiving a one-time code.
In scenarios where the passwordless option was used, credentials stolen by a stealer wouldn’t be sufficient to gain access. But a leaked UUID from the victim’s browser history still granted direct access to private user data, making broken access control the most effective path for the attacker to access user data.
3.2. The Blue Team Perspective on Responding to Stealer Logs
On the defensive side, discovering that credentials or tokens from the environment appear in a stealer log is a high-priority indicator of deeper compromise. Unlike commodity malware alerts, which might be quarantined and forgotten, a stealer log is proof that exfiltration occurred, and possibly that access is being resold or reused.
This reality means that traditional playbooks, which often stop at isolating the endpoint and resetting a password, are no longer sufficient. A broader lens is required, because once credentials are exfiltrated, the attack surface extends far beyond the initial device, potentially enabling access to web portals, internal tools, VPNs, or any third-party services where those same credentials may still be valid.
In practice, adopting this broader lens means asking a new set of forensic questions: Where else were these credentials used? Are the stolen session cookies still valid, potentially allowing attackers to bypass MFA? Has the account been accessed from unknown IPs or geographies? Without these answers, defenders risk overlooking silent, credential-based persistence.
Blue Team Note: Finding the Infection's Fingerprints
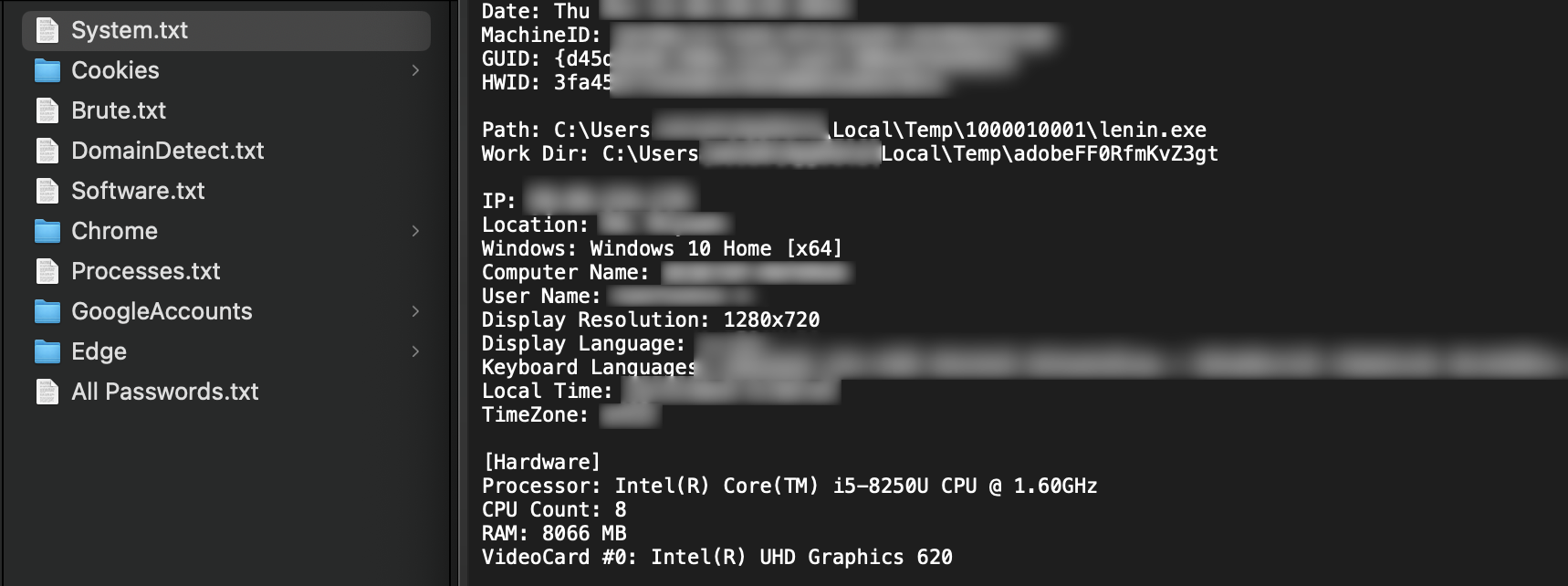
As an additional note, beyond the reactive measures of managing the resulting security risks, the stealer log itself can, in certain situations, become a direct source of information for obtaining Indicators of Compromise (IoCs). This involves looking past the stolen credentials and examining the operational artifacts left behind by the malware's execution.
Valuable forensic clues can often be found within bundled files like system.txt or information.txt. Instead of just seeing a list of stolen passwords, a defender might find:
- Suspicious file paths or executable names that point directly to the malware on disk.
- A list of running processes.
- Known malicious domains or C2 server addresses tucked away in browser history files.
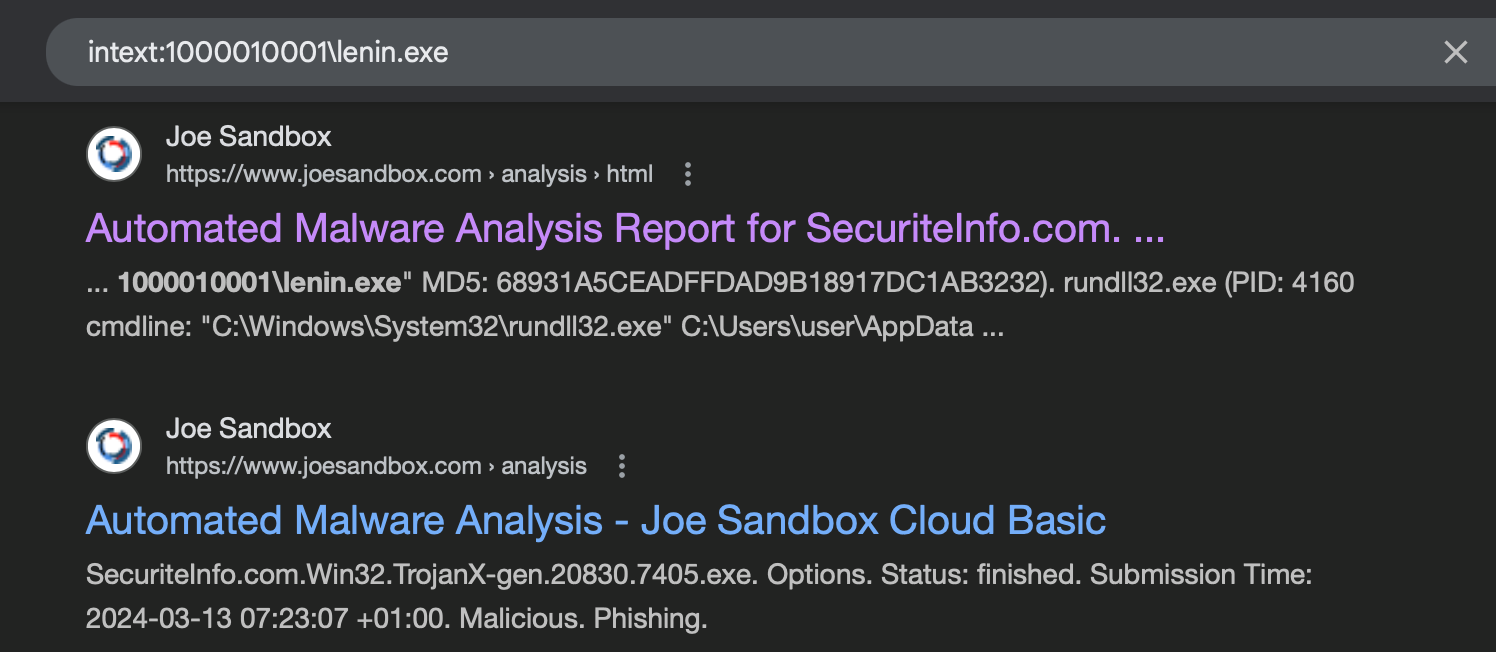
With a potential malware name and path in hand, the investigation can begin. A simple search online often immediately links these artifacts to known malware campaigns, as documented by other researchers or automated analysis platforms.
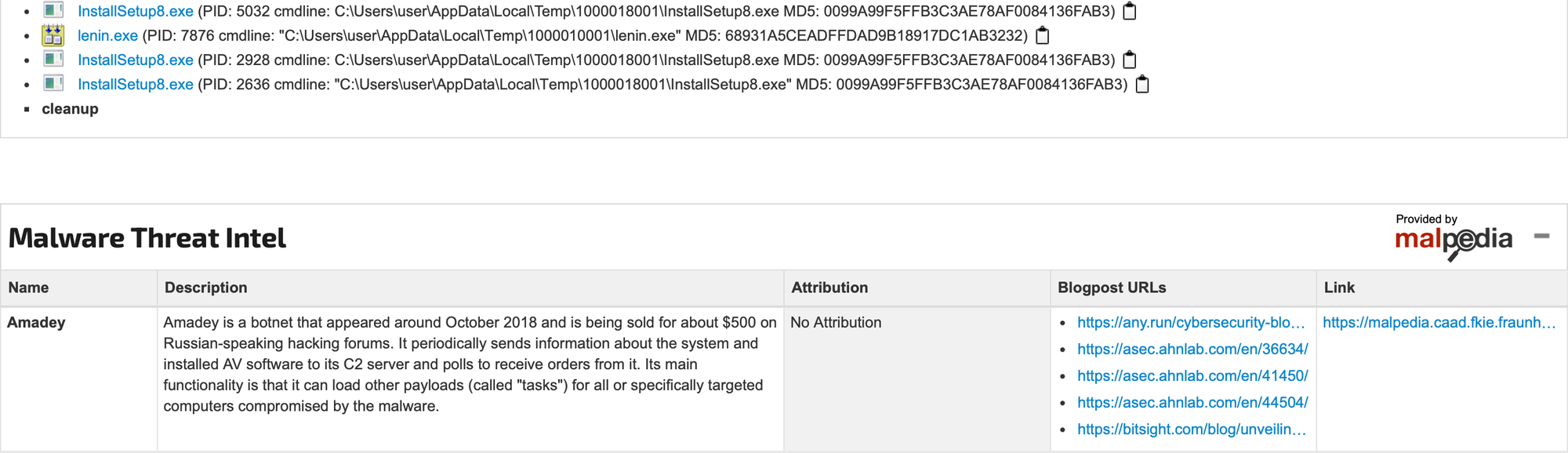
The malware’s hash can also be checked against VirusTotal to obtain additional insights into how various security vendors classify the file.
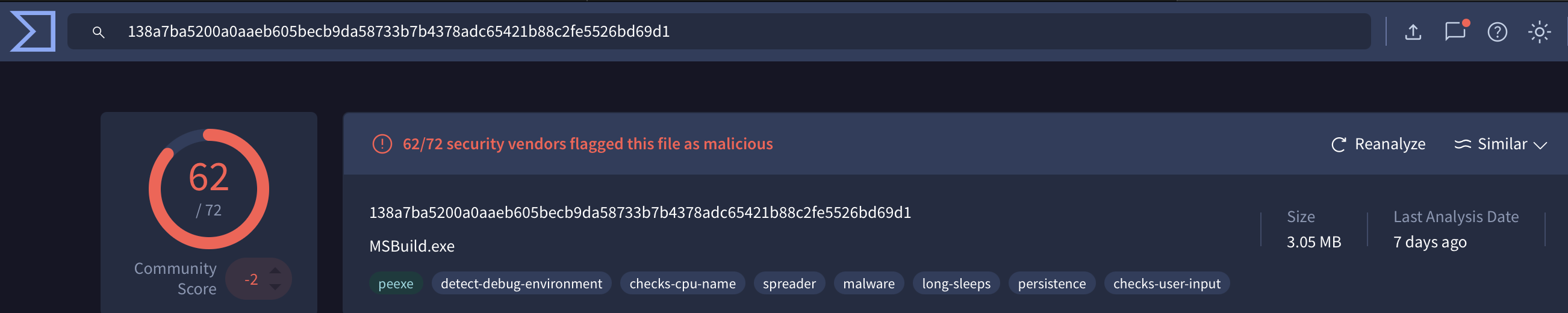
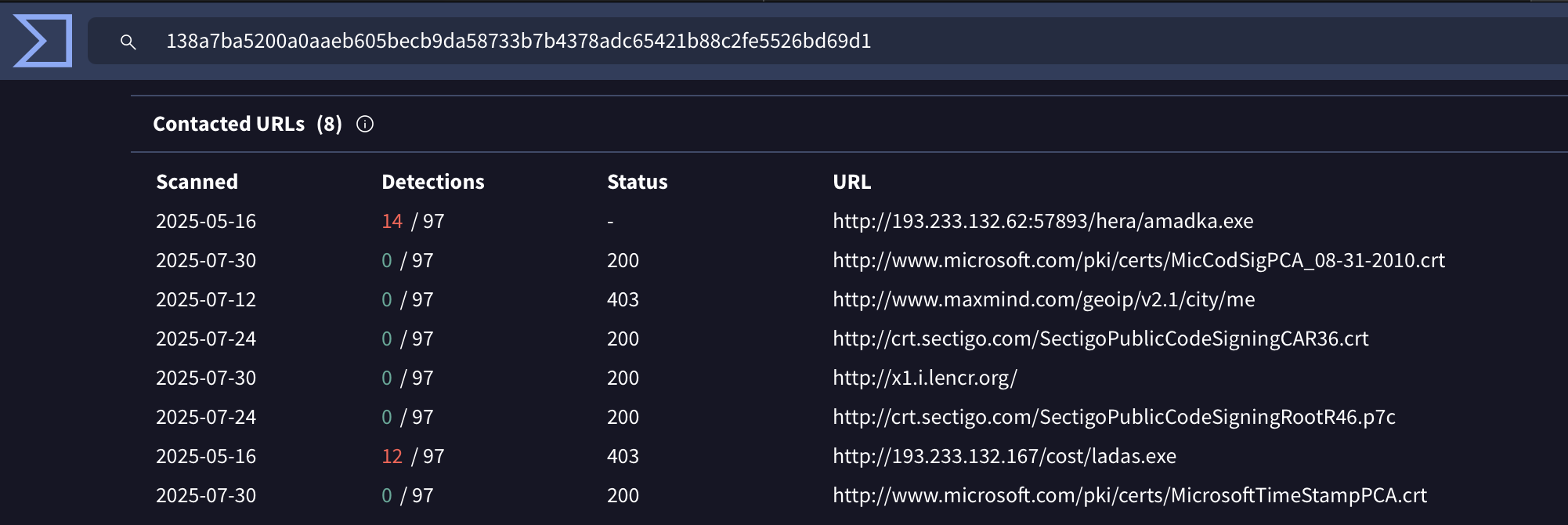
Nevertheless, once potential IoCs like file hashes, paths, or domains are validated, they become tangible assets for proactive defense. This intelligence enables security teams to hunt for the specific threat across the company, create robust endpoint detection rules (e.g., YARA), and block the associated malicious infrastructure.
In essence, leveraging the log in this manner effectively transforms it from a simple alert about a data leak into a source of high-fidelity intelligence, allowing a holistic response that not only manages the symptom but also helps eradicate the root cause.
So, by adopting this two-pronged approach, simultaneously tracking the compromised credentials downstream while hunting the source malware upstream, forms the foundation of a mature incident response program. It ensures that for any known compromise, a security team can effectively address both the immediate symptoms and the root cause.
Building on this foundation, defense teams should evolve their approach towards a more proactive strategy. This means they should treat stealer logs not just as records of past compromises, but as a vital source of external threat telemetry, an indicator of what adversaries know and could potentially use.
In practice, this involves systematically ingesting stealer datasets into detection pipelines to be cross-referenced against the internal environment. This includes both mapping exposed credentials to known employees and using discovered malware artifacts (like file hashes and C2 domains) for proactive, enterprise-wide threat hunting. This proactive stance makes it possible to spot and neutralize credential-based intrusions before they escalate, even if they bypass traditional malware defenses.
Equally important is coordination. If the exposed credentials belong to a third-party vendor, then security extends beyond your network. Incident response in these cases may require engaging with partners, rotating shared secrets, and reviewing logs in systems you don’t fully control.
4. Streamlining Stealer Log Analysis
4.1. The Analysis Bottleneck: Drowning in Data
The "Leaky Browser Profile" case we explored earlier is a stark reminder of how easily a corporate credential can land in an attacker's hands, all from a single stealer log, triggered by something as trivial as downloading a gaming cheat on a home PC.
Now, imagine facing not just one log, but an entire dump containing data from hundreds of different devices. The challenge immediately shifts from a simple treasure hunt to surviving an avalanche of information.
Faced with this avalanche, an analyst’s process becomes a brute-force search for relevance. The typical starting point isn't a specific “device” folder, it’s the raw passwords.txt (or similar) files inside each one. The work is a painfully manual grind, open a wall of text, Ctrl+F for keywords like @company-domain.com, vpn, or internal, and repeat across hundreds of folders, each representing a different compromised machine.
A fair question at this point is, "Why not just automate this?"
It's true that a custom script can be written to scan for specific keywords and pinpoint the exact directory (or "device") containing the target information. And while this certainly speeds up initial filtering, it often stops at surface-level matches. It’s a helpful shortcut, but one that still requires an analyst to manually open raw files, leaving the door open for missed context and repetitive effort.
This workflow creates a major capability gap. While large enterprises can absorb this complexity with custom tooling and dedicated teams, the reality for most security professionals, researchers, understaffed SOCs, and smaller businesses is that they are left relying on manual processes that don’t scale, putting them at a serious disadvantage in a fast-moving threat landscape.
4.2. Introducing Broń Vault
What if, instead of writing ad-hoc scripts, you could just drag and drop entire .zip files into a simple web-based tool? Imagine a tool that instantly extracts and structures the credentials for quick searching, while still preserving full access to the entire original log: every cookie, system file, and browser artifact, all in one place.
That is the question that led to the creation of Broń Vault, an open source stealer logs dashboard.
Broń Vault is our answer to a challenge we see every day in the industry, which is, how to effectively serve the day-to-day needs of security teams on the front lines, who often lack a straightforward alternative to manual scripting or complex platforms. It reflects our core mission at PT ITSEC Asia Tbk to democratize security, making foundational capabilities accessible to everyone. Our goal is to eliminate the grunt work of log parsing, so you can focus on what truly matters: making critical security decisions, fast.
Here is a brief overview of its core features:
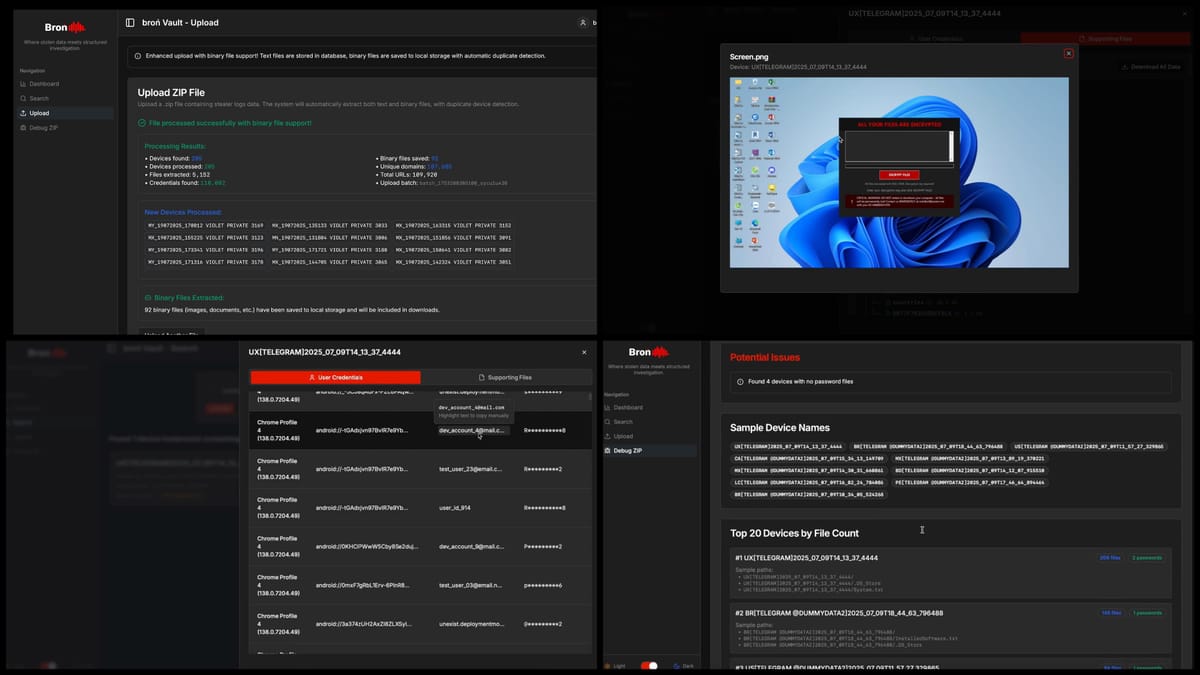
A. Getting Started: Uploading and Validating Data
Getting started with Broń Vault is designed to be as simple as possible. Forget complex setups or command-line gymnastics. You can simply drag and drop your .zip log files directly into the Upload interface. Broń Vault handles the rest, automatically parsing and structuring the data in the background, making it immediately available for analysis through the Dashboard and Search modules.
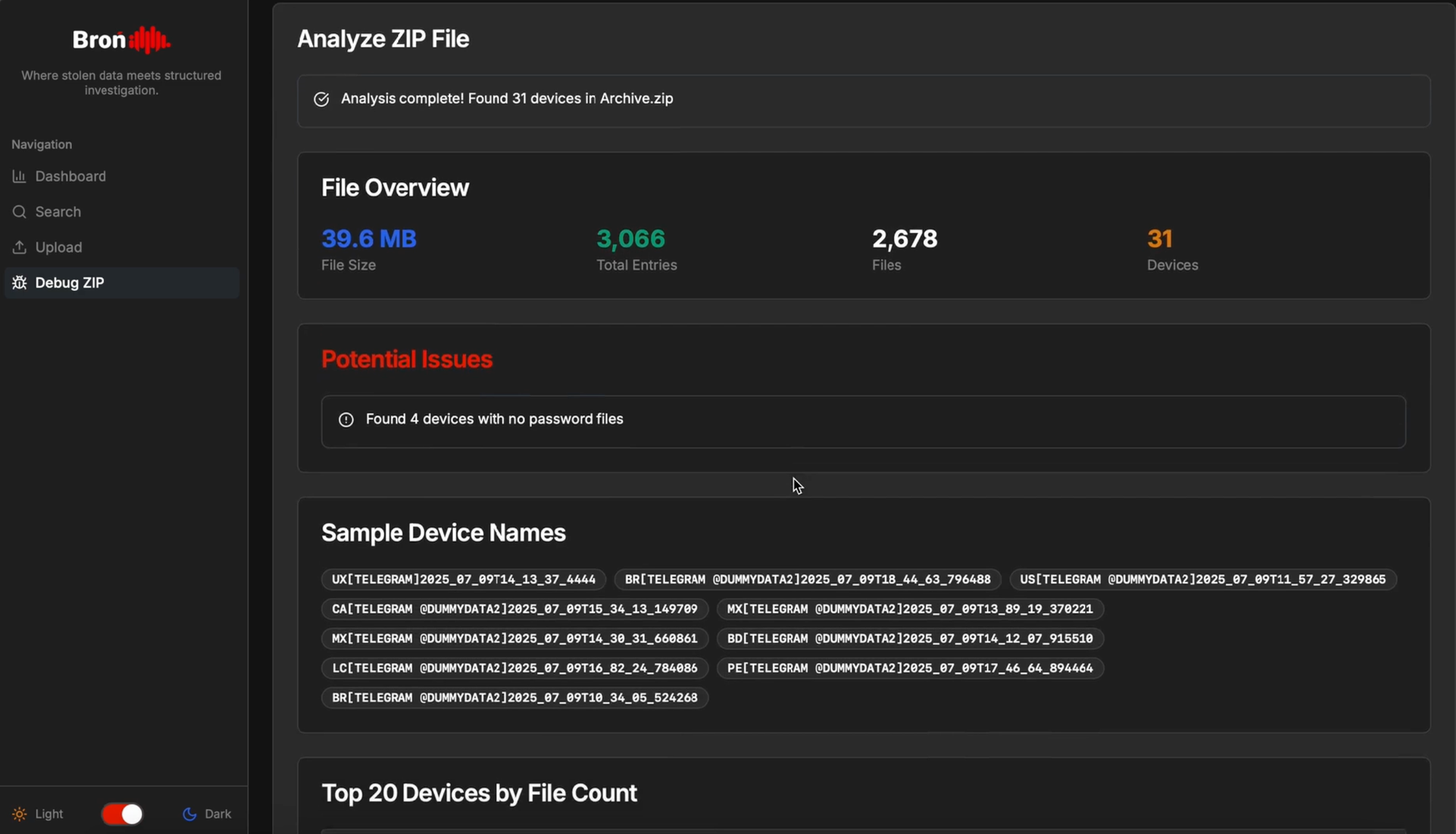
But what if we’re unsure whether a file follows the structure commonly used by threat actors?
For situations where we’re dealing with unfamiliar or potentially incomplete archives, we've also included a lightweight Debug-Zip utility. This tool lets us to perform a quick pre-flight check on any .zip file, analyzing its internal structure to see if it matches typical stealer formats. Importantly, it also flags any device directories that are missing a password file (passwords.txt or equivalent), which can often indicate a corrupt or low-value log. It’s a fast way to triage incoming files, so you can proceed with confidence and focus on what matters.
B. The 30,000-Foot View (Dashboard)
Instead of drowning you in a wall of text, Broń Vault immediately presents a high-level Dashboard. This gives you an instant strategic overview of the entire dataset, answering critical questions at a glance: How many devices and credentials are in this dump? What are the most common passwords that could indicate weak patterns? Which top-level domains (.tld) are most affected? What are the most common browsers or software being used, hinting at potential attack vectors?
Under the hood, we’ve already separated key components typically found in stealer logs, for example, credentials (including TLDs, domains, and browsers stored in distinct fields) and installed software.
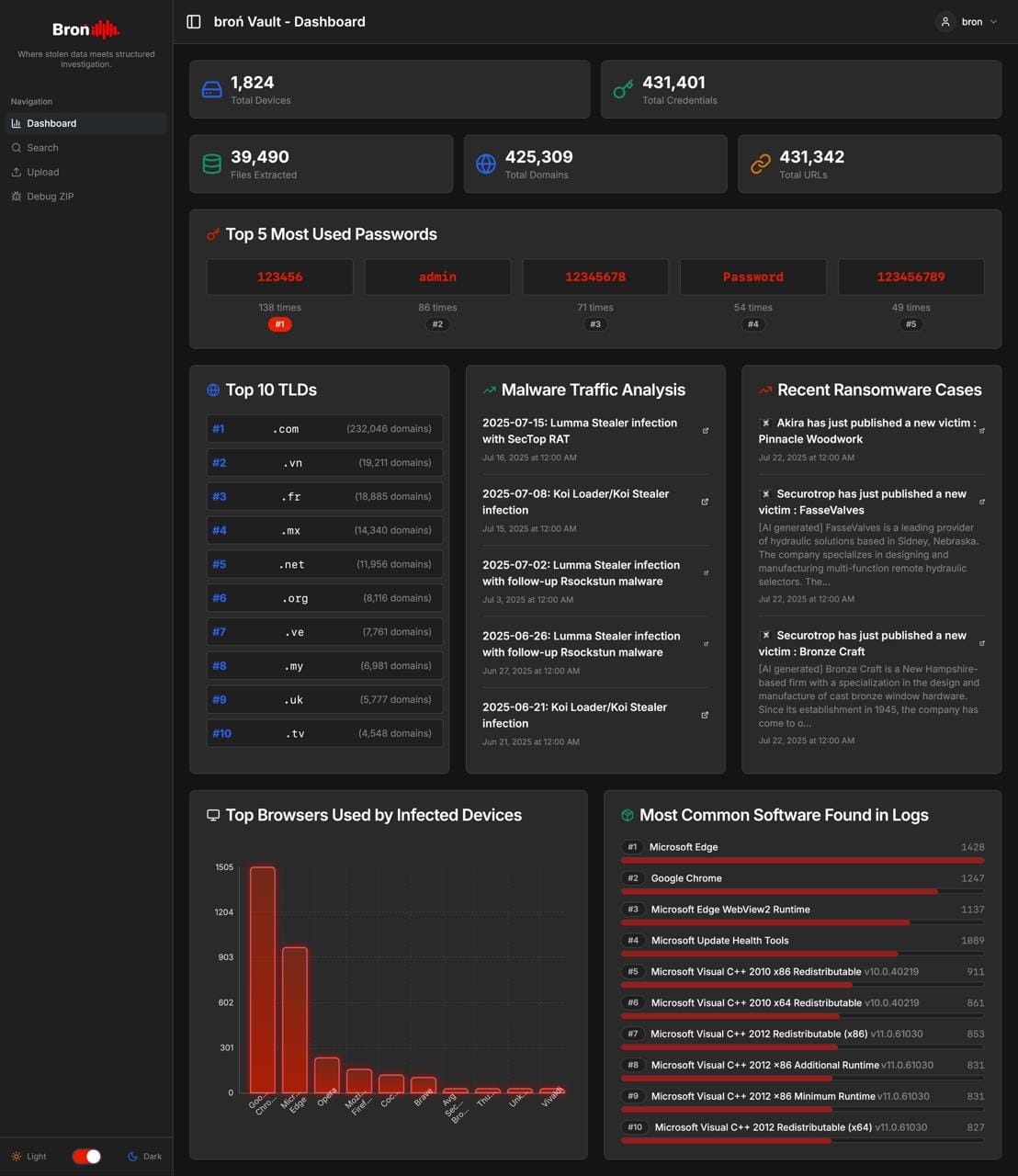
Technically, this architecture is extensible by design. For example, correlating infection-time IPs could enable future features like regional threat mapping. In short, Broń Vault is designed not as a static tool, but it is a living, evolving open-source project.
C. Powerful, Correlated Search (Search)
This is the core of Broń Vault. The Search functionality is built to eliminate the nightmare of manual correlation. You can perform lightning-fast lookups by domain (e.g., company-domain.tld) or email, and this is where the real value starts to unfold.
Instead of showing just a plain line of text, a successful match displays the credential along with a tab of correlated data labeled “Supporting Files”. This tab reveals all other files stolen from the same device. With a single click, you can pivot from a discovered password to viewing the victim’s browser history, inspecting stolen cookies, or exploring other extracted files, all without ever leaving the interface.
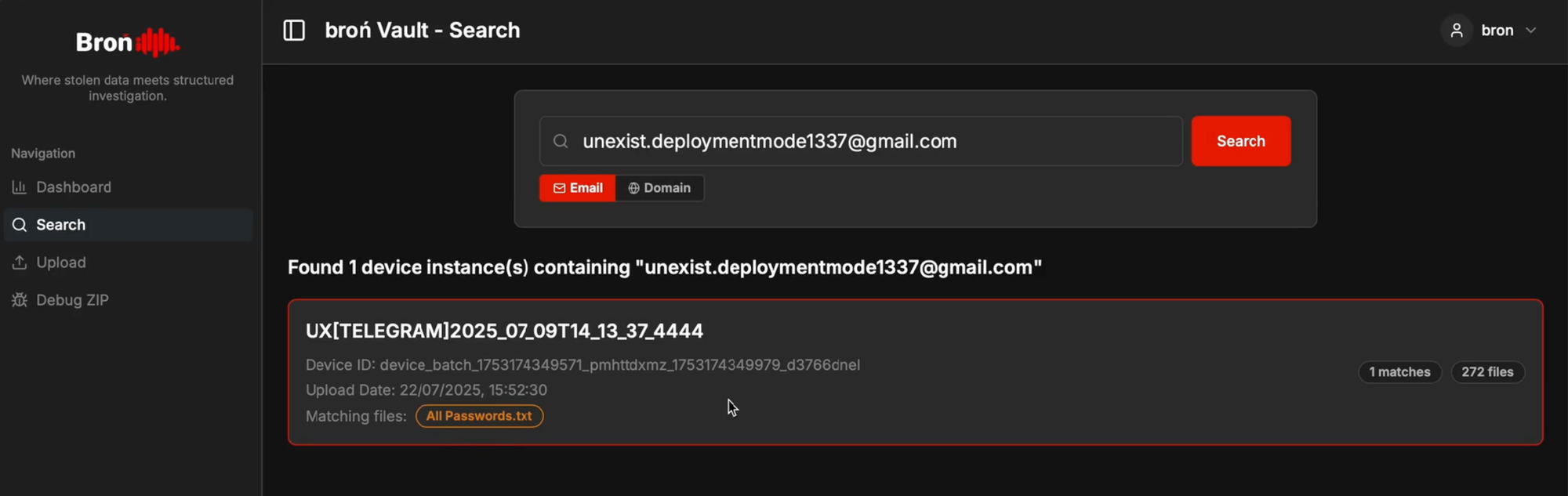
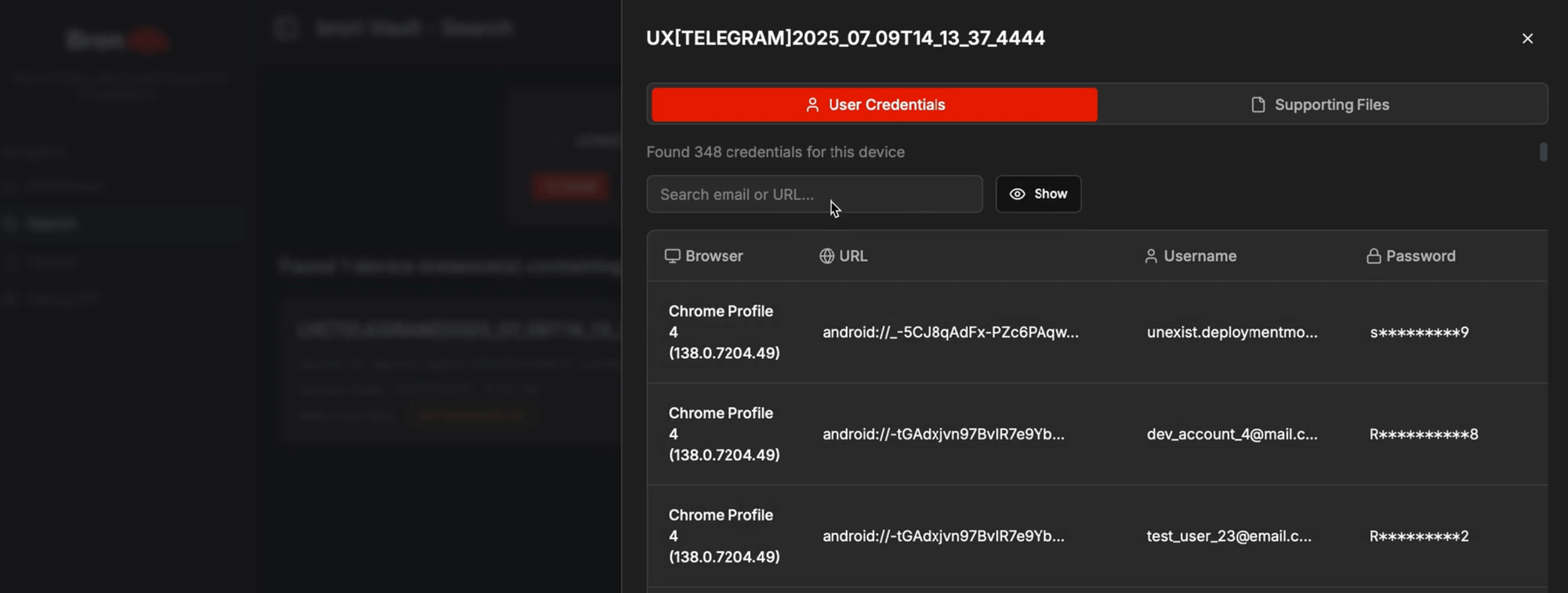
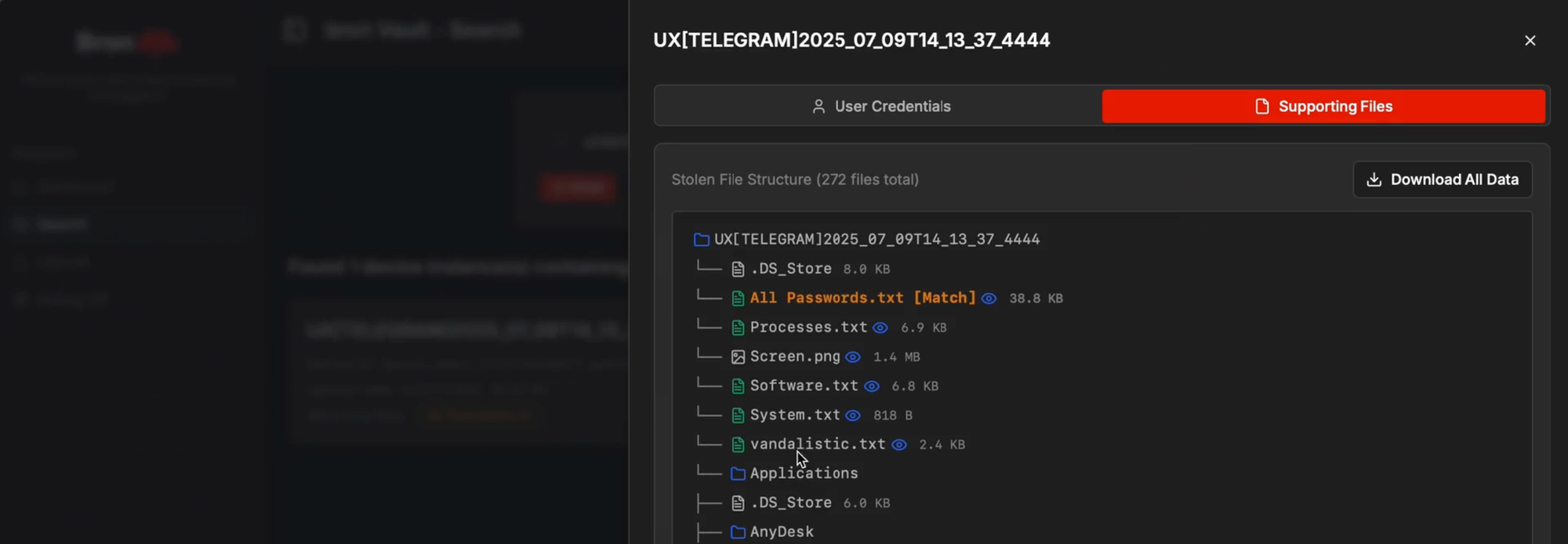
What used to be a painful process of connecting the dots, now becomes a seamless and intuitive workflow.
5. Summary and the Road Ahead
Stealer malware may not generate the same headlines as a ransomware outbreak or a zero-day exploit. This, however, is precisely what makes it so insidious. It has become a full-scale, silent epidemic, operating beneath the surface of mainstream attention, yet fueling the very attacks that do make the news.
Throughout this article, we’ve explored how these logs reshape both offensive and defensive operations. They offer attackers a path of least resistance around hardened defenses, and provide defenders with a raw collection of investigative leads from the compromised device. More than that, they have also raised uncomfortable questions about where the corporate security boundary truly lies, especially as personal and professional digital lives increasingly blur.
Looking forward, we also recognize that as organizations grow, their security needs often evolve towards more automated and integrated workflows. To support this very journey, our mission to democratize security extends to a dedicated technology platform and managed services designed to address these evolving needs. These solutions offer a more comprehensive approach, including large-scale data ingestion, curated threat intelligence, and proactive alerting, all designed to help teams of any size mature their security posture and stay ahead of emerging threats.
REFERENCES
- Verizon, “2025 Data Breach Investigations Report,” Basking Ridge, NJ, USA, May 2025. [Online]. Available: https://www.verizon.com/business/resources/reports/dbir/
- MyCERT, “MA-906.012023: MyCERT Advisory - New Dark Pink APT Group Targets Government and Military Organisations in APAC Countries,” Jan. 18, 2023. [Online]. Available: https://mycert.org.my/portal/advisory?id=MA-906.012023.
- Australian Signals Directorate, "The Silent Heist: Cybercriminals Use Information Stealer Malware to Compromise Corporate Networks," Sep. 2, 2024. [Online]. Available: https://www.cyber.gov.au/about-us/view-all-content/alerts-and-advisories/silent-heist-cybercriminals-use-information-stealer-malware-compromise-corporate-networks
- Y. Kho, “Understanding Stealer Logs and Their Role in Security Testing — Part 1,” Medium, Aug. 30, 2024. [Online]. Available: https://medium.com/@YoKoKho/understanding-log-stealer-and-its-role-in-security-testing-part-1-5f2223b47847
- A. Mukherjee, "How Stealer Malware Puts Your Credentials at Risk," Jul. 3, 2023. [Online]. Available: https://www.threatintelligence.com/blog/stealer-malware.
- S. Sharma and A. Kumar, "Statc Stealer: Decoding the Elusive Malware Threat," Aug.8, 2023. [Online]. Available: https://www.zscaler.com/blogs/security-research/statc-stealer-decoding-elusive-malware-threat.
About the Authors
This article and the accompanying Broń Vault dashboard were jointly written and developed by Tomi Ashari and me as part of internal research by the ITSEC Asia R&D Division.