Akira (also known as REDBIKE) has emerged as one of the most disruptive ransomware operations targeting small-to-medium-sized businesses (SMBs) across North America and Europe. Since its appearance in 2023, Akira has extorted more than $42 million from over 350 confirmed victims, according to a Joint Cybersecurity Advisory by US and European authorities.
Unlike typical affiliate-based ransomware models, Akira functions more like a centralized operation, echoing the structure of the former Conti syndicate. Several financially motivated threat clusters, including UNC5277 and UNC5280, have been observed leveraging REDBIKE to extort victims, demonstrating the group’s appeal to multiple actor sets. Its operators continue to refine tactics while expanding across Windows, Linux, and ESXi environments.
To better understand how Akira operates in practice, we also examined technical samples associated with this ransomware. The following section highlights file artifacts, indicators of compromise, and cryptographic mechanisms identified through open-source enrichment and malware analysis.
Technical Details
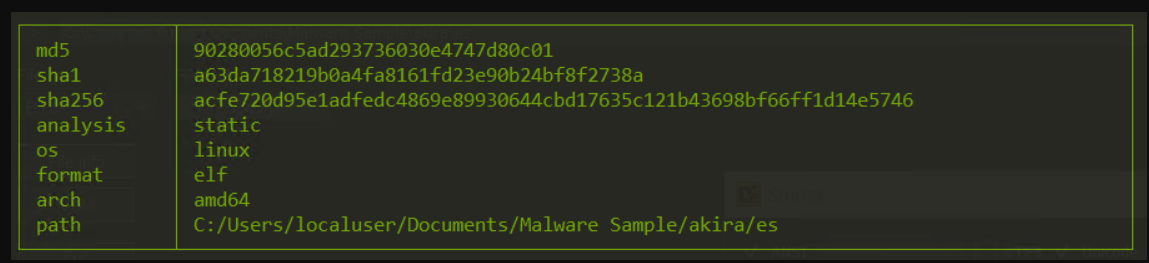
Filename : es
Hash:
- MD5: 90280056c5ad293736030e4747d80c01
- SHA1: a63da718219b0a4fa8161fd23e90b24bf8f2738a
- SHA224: 4f73f87d078a7eb3e899eef99daf4b740170d762661fc0740902fe9b
- SHA256: acfe720d95e1adfedc4869e89930644cbd17635c121b43698bf66ff1d14e5746
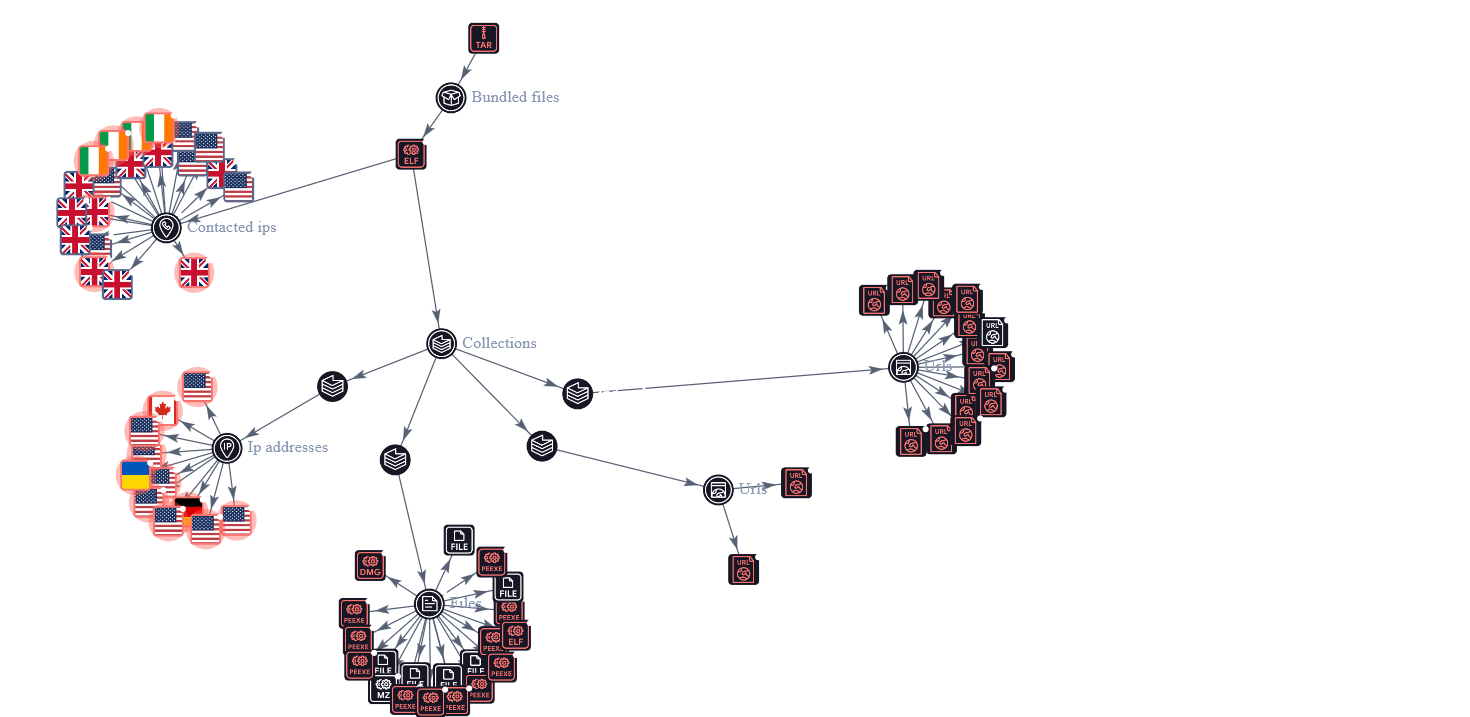
Below detail the relation of Akira ransomware based on Virustotal data, this file was contacted malicious IP's with difference regions, and also get the enrichment from the community related the Akira IoC.
Capa Analysis
Below the result of capa analysis, Akira have some Cryptography mechanism that detected by Capa signature like AES and RC4 and also have some obfuscation mechanism to evade detection.
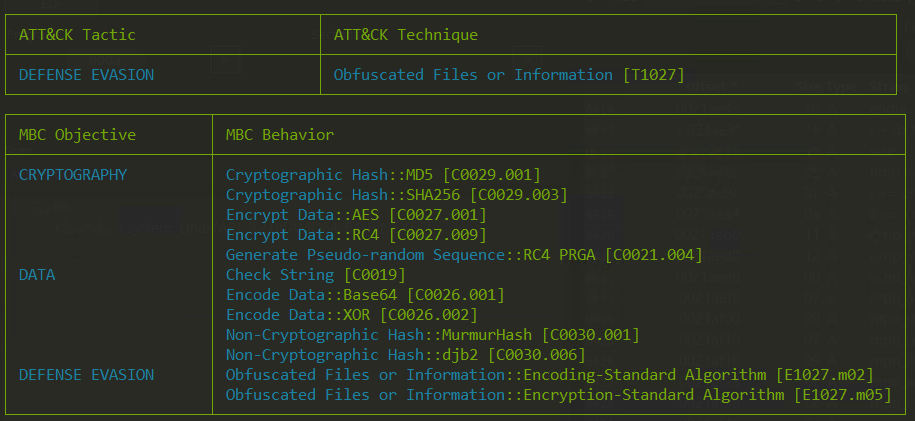
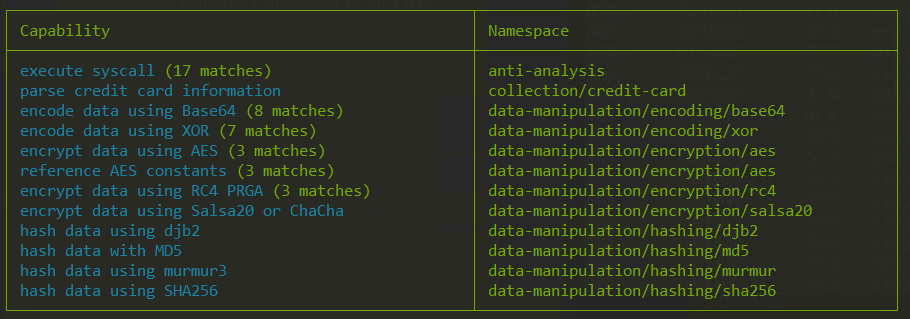
Static Analysis
This is the report of static analysis this malware, based on this analysis few information has been discovered related the library that used by the malware, extensions that targeted, the ransomware notes and especially how this malware handle the encryption process.
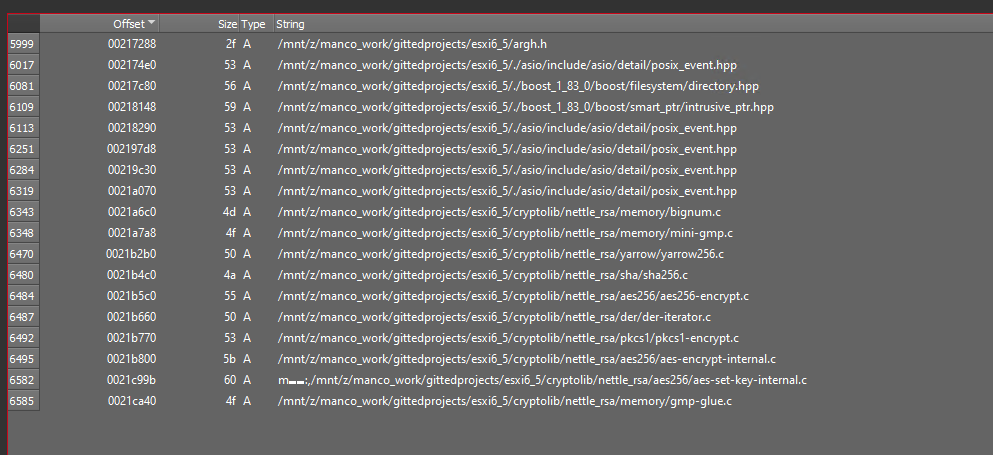
The filenames reveal the exact software libraries the threat actor used to build the ransomware's encryption engine.
- Nettle Cryptography Library: The path
.../cryptolib/nettle_rsa/...shows they used Nettle, a well-known cryptographic library. The files listed are the building blocks of their encryption scheme:aes256-encrypt.c: Used for AES-256 encryption. This is a symmetric algorithm, meaning it's very fast and is used to encrypt the actual files.pkcs1-encrypt.c: Used for RSA encryption (specifically the PKCS#1 standard). This is an asymmetric algorithm, used to encrypt the much smaller AES key. This hybrid approach is standard for ransomware.sha256.c: Used for SHA-256 hashing, likely to verify data integrity.yarrow256.c: Used a Yarrow random number generator to create cryptographically secure random numbers for the encryption keys.mini-gmp.c: Used the GNU Multiple Precision (GMP) library, which is necessary for the complex mathematics behind RSA encryption.
- Asio Library: The path
asio/..., which is used for networking and input/output operations.
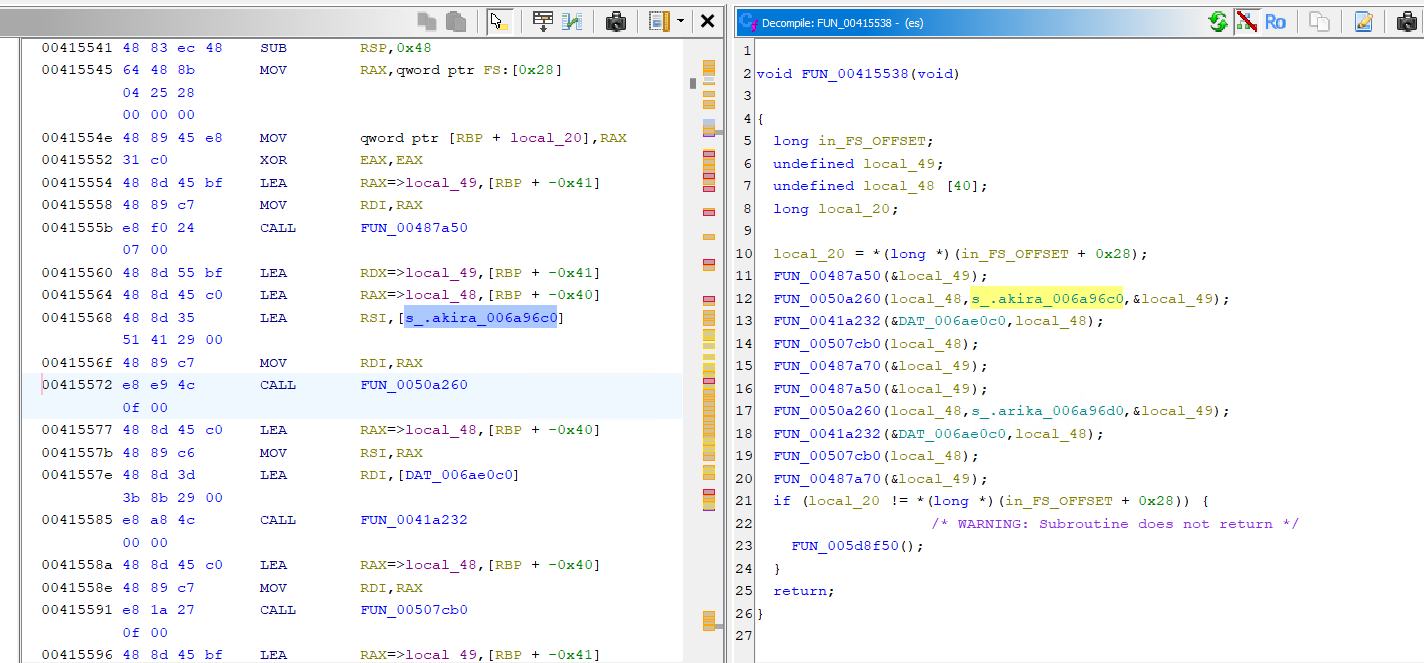
Files encrypted by this particular strain of malware are identifiable by a file extension .akira. This is a clear indicator of compromise, allowing users and security professionals to quickly ascertain which files have been affected by Akira Ransomware.
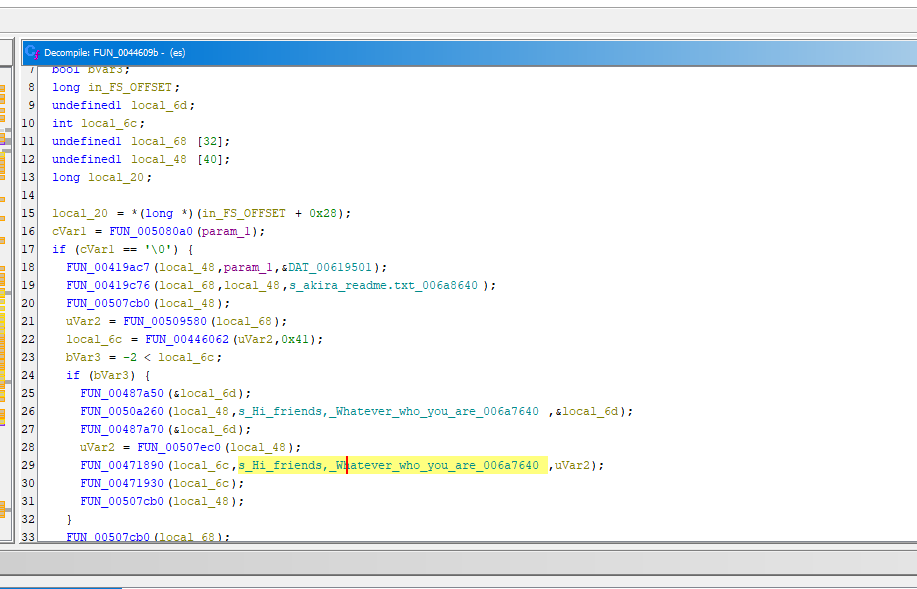
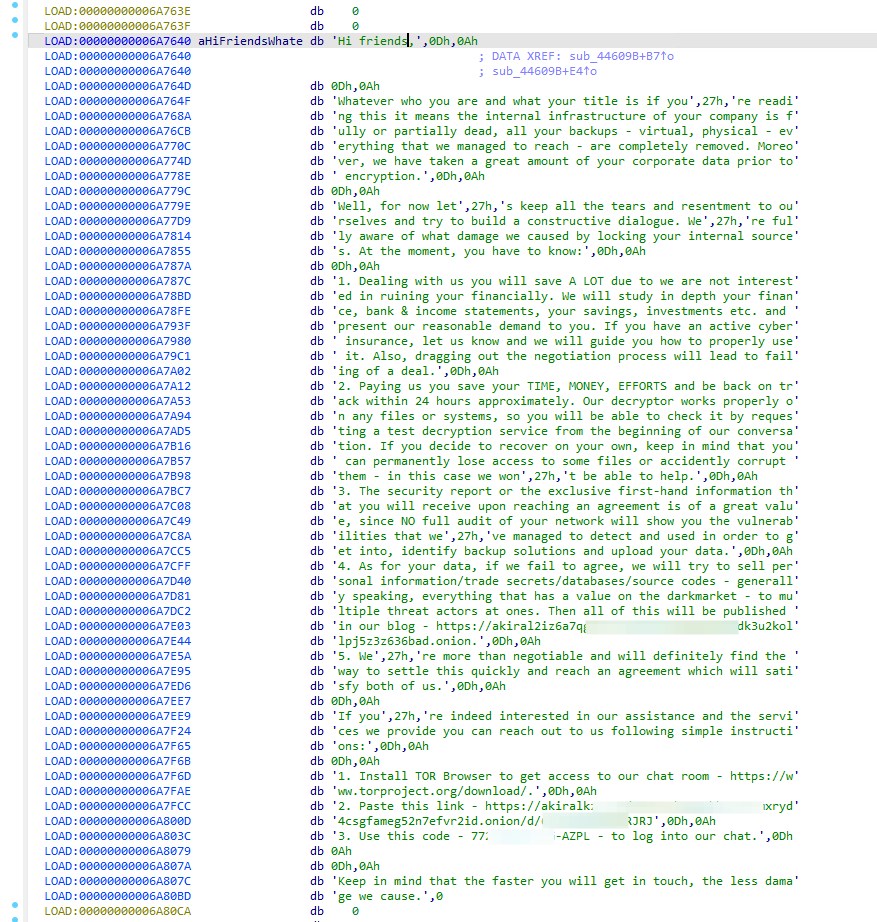
Akira generates a ransom note in the form of a text file named "akira_readme.txt." This note includes a URL for negotiating with the threat actor.
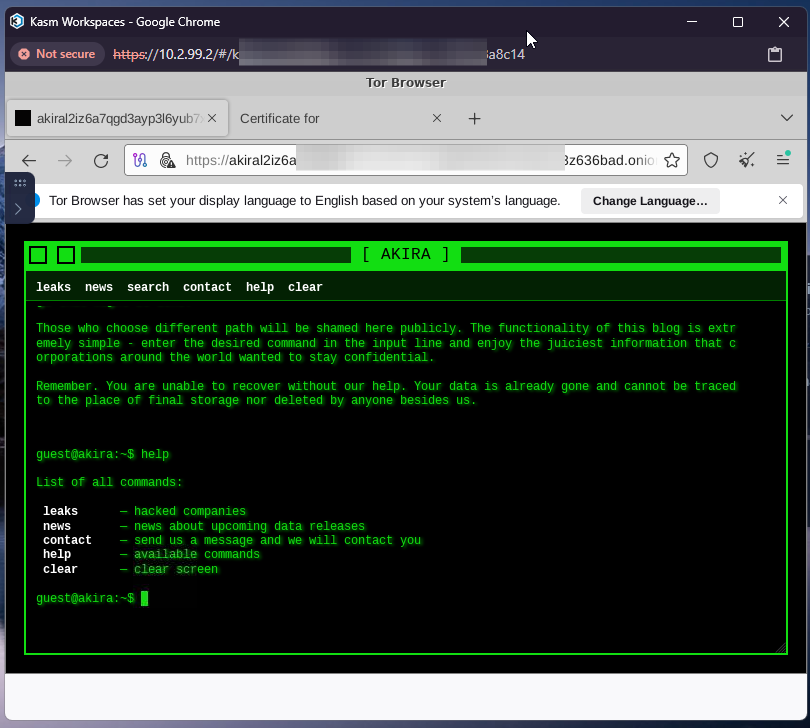
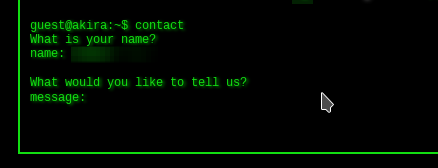
The Akira blog page, where you can find the latest breaches by the threat actor, remains accessible.
Targeted File Extensions
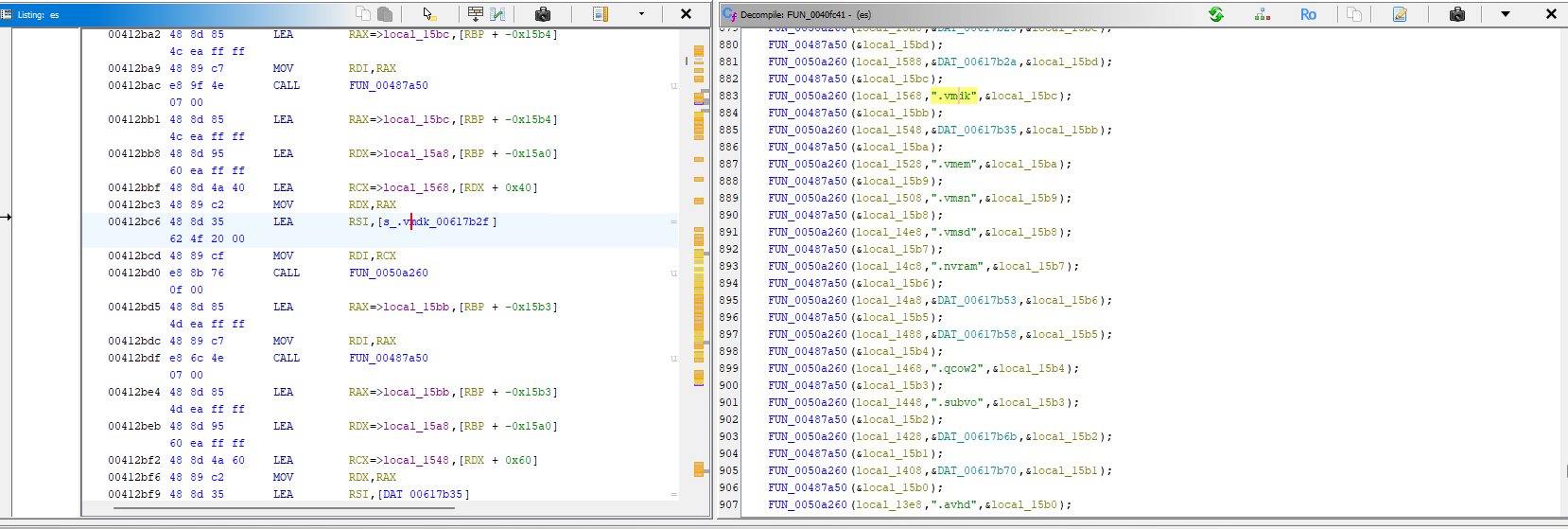
Static analysis revealed that this malware affects numerous extensions, ranging from database to VM files, as listed below.
Extensions
Microsoft Access:
.accdb, .accdc, .accde, .accdr, .accdt, .accft, .accdw
SQLite Variants:
.sqlite, .sqlite3, .sqlitedb, .db, .db-shm, .db-wal
Virtual Machine Files (20 extensions)
VMware:
.vmdk (Virtual Disk)
.vmem (Memory snapshot)
.vmsn (Snapshot)
.vmsd (Snapshot metadata)
.nvram (BIOS/UEFI state)
.vmx (Configuration)
.vmxf (Team configuration)
.vmrs (Resource)
Hyper-V:
.vhdx (Virtual Hard Disk v2)
.avhd (Differencing disk)
.avdx (Checkpoint disk)
.vmcx (Configuration)
QEMU/KVM:
.qcow2 (QEMU Copy-On-Write v2)
VirtualBox:
.vdi (Virtual Disk Image)
.vbox (Configuration)
...
...Command Line Arguments
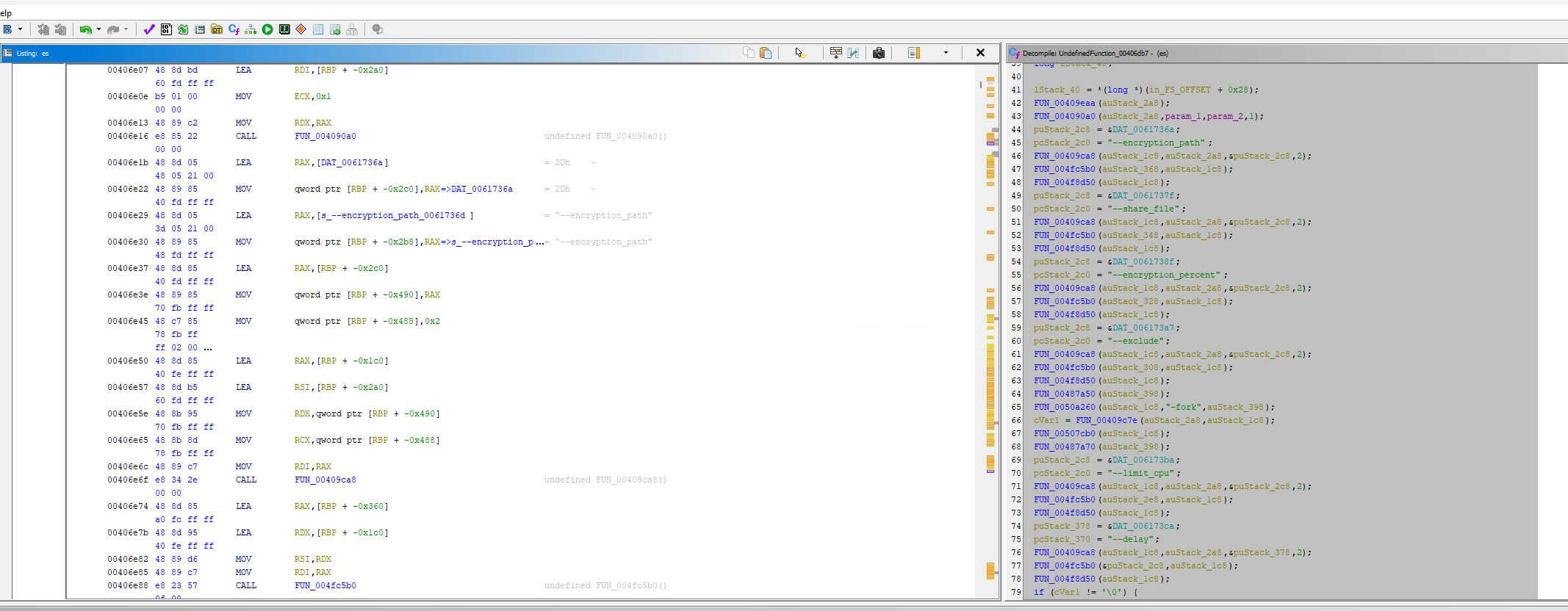
This ransomware implements a sophisticated command-line interface allowing operators to customize attack parameters for different scenarios. Each flag modifies specific behavioral aspects of the malware's execution.
--encryption_path # Target directory to encrypt
--share_file # Shared key/configuration file
--encryption_percent # Percentage of file to encrypt (performance optimization)
--exclude # Exclusion patterns
--limit_cpu # CPU usage throttling
--delay # Delay between operations
-fork # Fork process (daemonize)Cryptosystem
This variant of Akira ransomware employs a hybrid cryptosystem combining ChaCha20, AES-256, and RSA-4096, with the Nettle library managing its cryptographic operations. The process begins by encrypting the symmetric decryption key with RSA-4096. This resulting 512-byte encrypted key is then placed at the beginning of the file as its first block. Subsequently, the actual file content is encrypted using the ChaCha20 stream cipher, which processes the data in (0xFFFF) blocks.
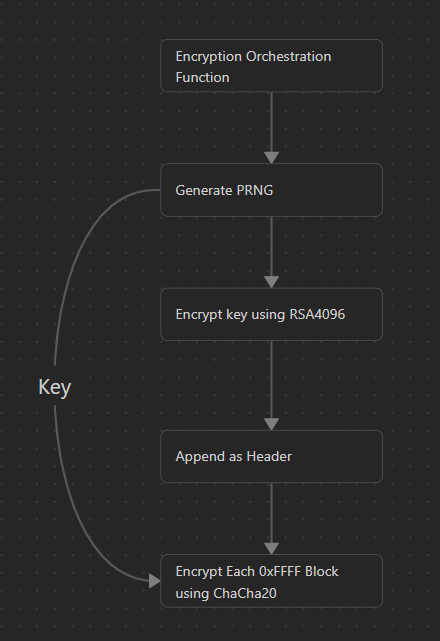
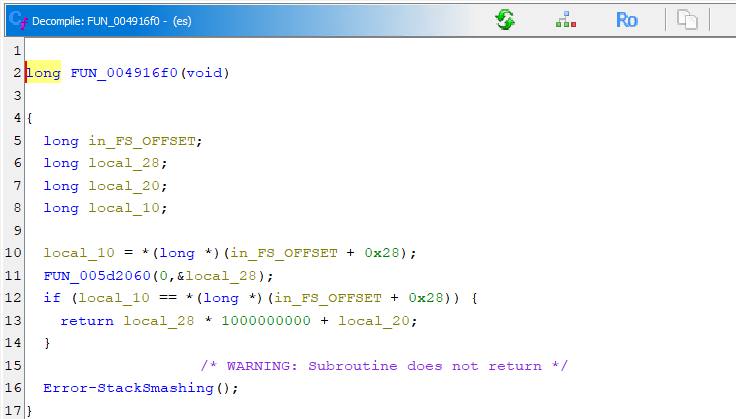
- Pseudo Random Number Generation
In this section we can examine how this malware generate seed using Yarrow algorithm. Based on this function malware used timestamp as PRNG for generating seed. This seed will used for the next key generation.
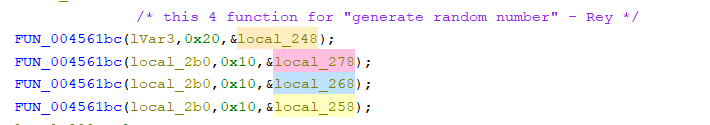
- How to split the file into blocks
This malware is split the encryption process by categorize by flag option and categorize file using their size, condition is for file under 2MB and higher than 2MB. file <2MB will used percentage for encryption process and >2MB will be used block pattern for encryption process. the partially encrypted mode using percentage mechanism and block pattern mechanism.
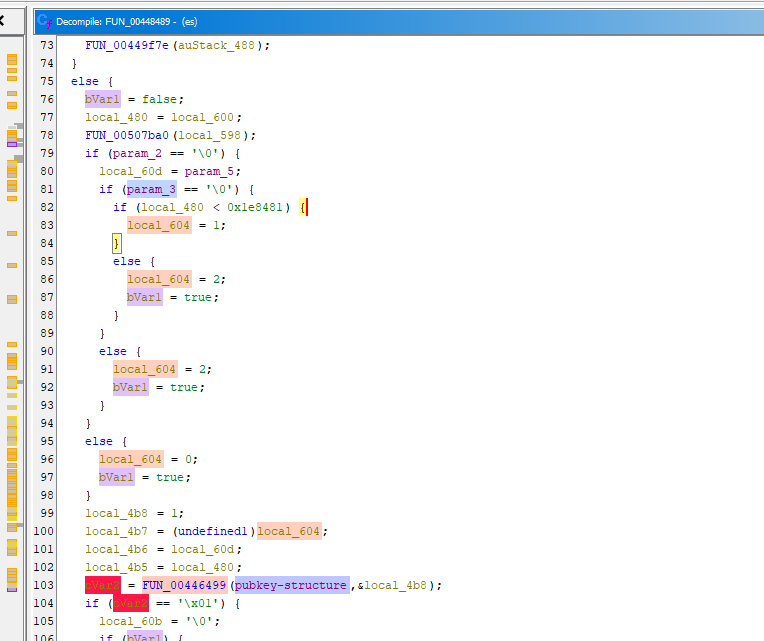
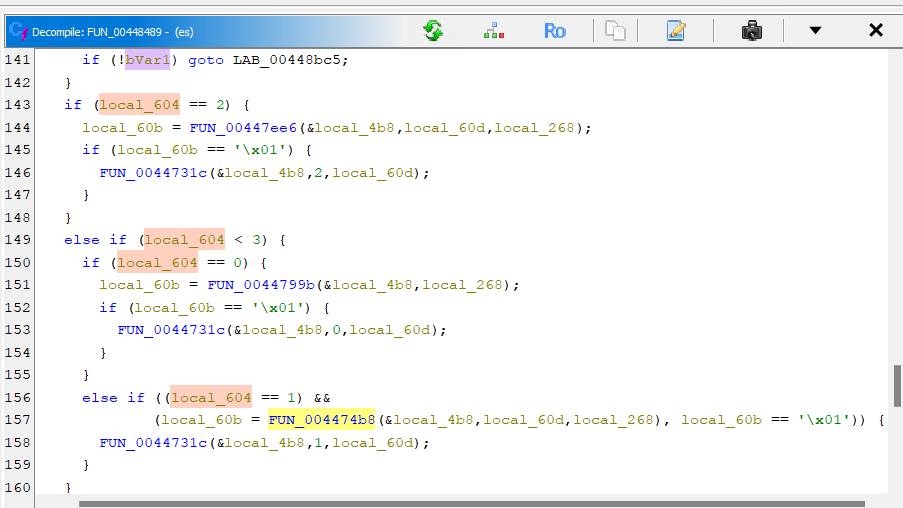
There is fully encrypted method at mode 0, that will full encryption by processing 0xFFFF bytes per-block.
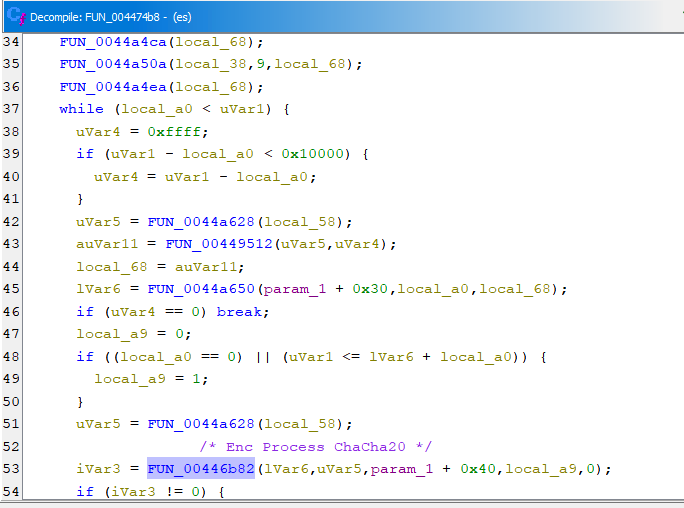
The percentage encryption at mode 1 will encrypted the file with some specific percentage which mean, if the percentage was 60%, the file will encrypted just 60% the rest will unencrypted. the encryption process will encrypt 0xFFFF bytes per-block.
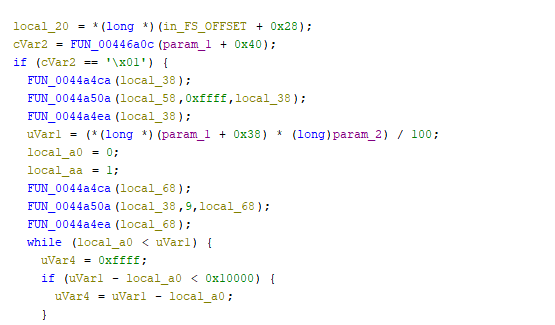
Original File: [HEADER][DATA.....................]
Mode 1 (50%): [XXXXXX][XXXX.....................]
↑ Encrypted ↑ ↑ Plaintext ↑Last mode is mode 2, in this encryption method data will split into block and encrypting each block. the encryption process will encrypt 0xFFFF bytes per-block.
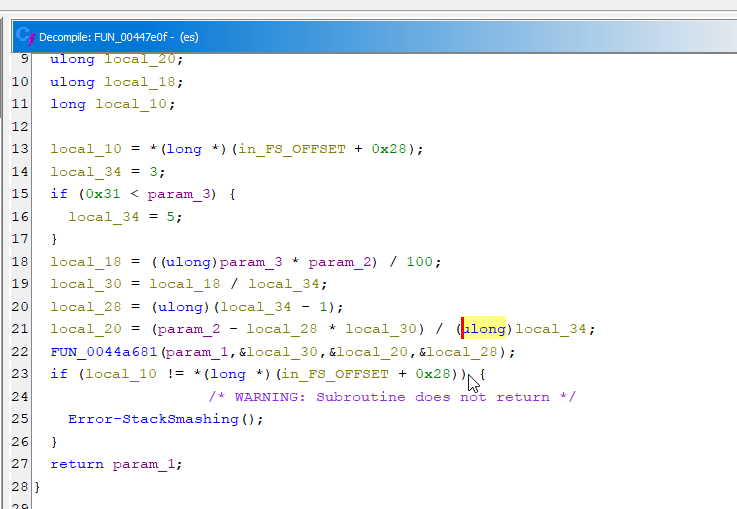
CRITICAL FINDING: This is ESXi ransomware specifically designed to encrypt VMware virtual machine files. The malware uses ChaCha20-CTR encryption of VM data.
Indicator Of Compromise
SHA256 hash for of Akira ransomware's Linux/ESXi variant
- ES - 90280056c5ad293736030e4747d80c01
Yara Rules
rule Akira_Ransomware {
meta:
description = "Detects ESXI Akira ransomware"
author = "Lalu Raynaldi Pratama Putra"
md5 = "90280056c5ad293736030e4747d80c01"
strings:
$arg1 = "--encryption_path" ascii
$arg2 = "--share_file" ascii
$arg3 = "--encryption_percent" ascii
$arg4 = "--exclude" ascii
$arg5 = "-fork" ascii
$arg6 = "--limit_cpu" ascii
$lib1 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/aes256/aes-set-key-internal.c" fullword ascii
$lib2 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/yarrow/yarrow256.c" fullword ascii
$lib3 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/sha/sha256.c" fullword ascii
$lib4 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/pkcs1/pkcs1-encrypt.c" fullword ascii
$lib5 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/aes256/aes256-encrypt.c" fullword ascii
$lib6 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/aes256/aes-encrypt-internal.c" fullword ascii
$lib7 = "/mnt/z/manco_work/gittedprojects/esxi6_5/cryptolib/nettle_rsa/der/der-iterator.c" fullword ascii
$xor_key = { 61 80 AF 48 5E FA A8 26 }
$onion1 = "akiralkzxzq2dsrzsrvbr2xgbbu2wgsmxryd4csgfameg52n7efvr2id.onion" fullword ascii
$onion2 = "akiral2iz6a7qgd3ayp3l6yub7xx2uep76idk3u2kollpj5z3z636bad.onion" fullword ascii
condition:
6 of ($arg*) and 7 of ($lib*) and 2 of ($onion*) or xor_key
}
References
- https://attack.mitre.org/groups/G1024/
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-109a
- https://www.cert-in.org.in/s2cMainServletpageid=PUBVA01&VACODE=CIVA-2023-2113
- https://tinyhack.com/2025/03/13/decrypting-encrypted-files-from-akira-ransomware-linux-esxi-variant-2024-using-a-bunch-of-gpus
- https://en.wikipedia.org/wiki/Salsa20
- https://cybersecuritynews.com/akira-and-lynx-ransomware/
- https://services.google.com/fh/files/misc/m-trends-2025-en.pdf
- https://www.ransomwarehelp.com/cybersecurity/akira-ransomware-in-2025/
- https://securitybrief.com.au/story/mandiant-report-reveals-ransomware-surge-evolving-tactics