with Renaldi Antonio
The internet is full of useful information, but not every website is safe. Some malicious sites secretly attempt to steal personal data without us even realize. And this time, we are trying to addresses this risk by creating a DNS Resolver App.
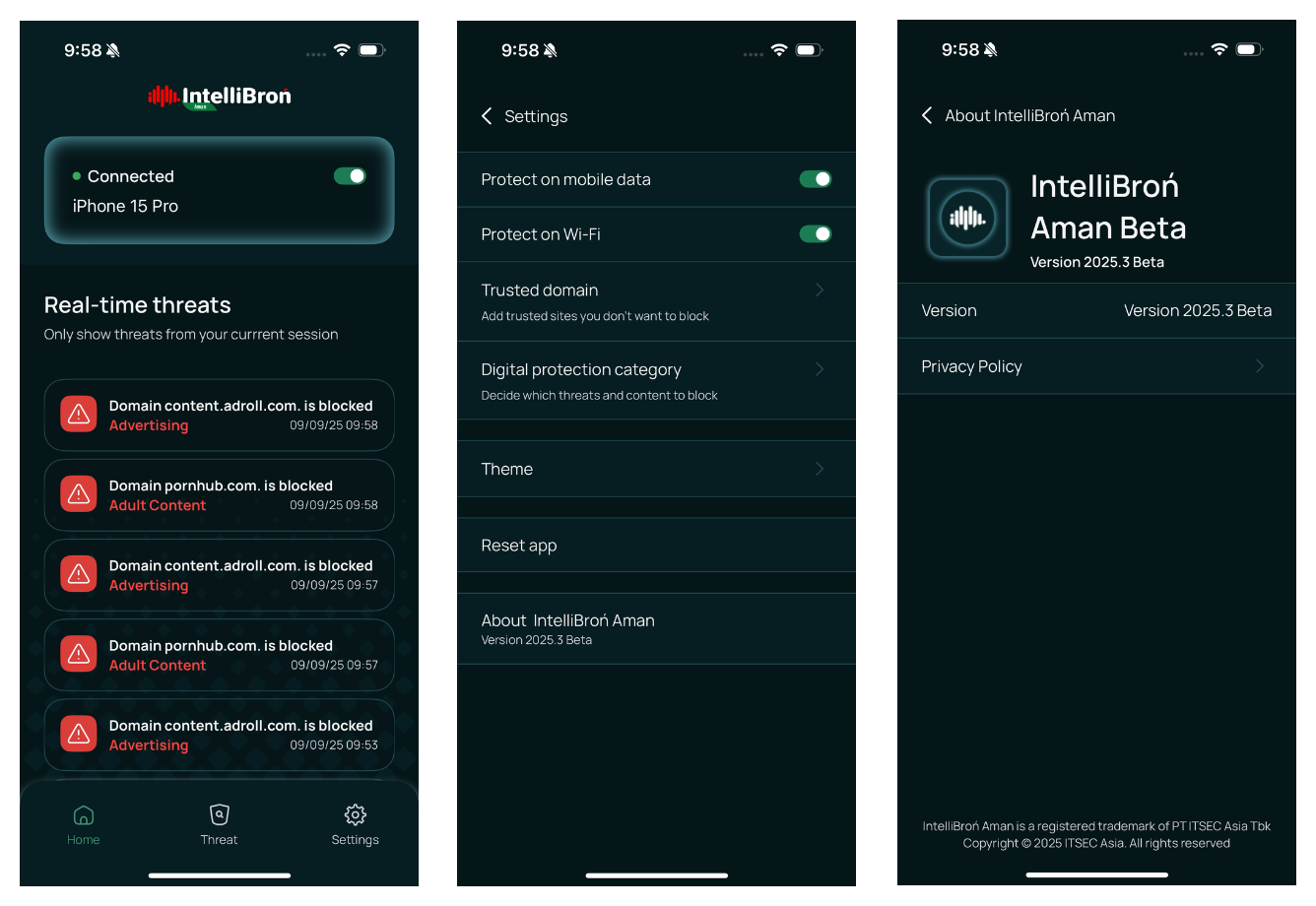

How DNS works?
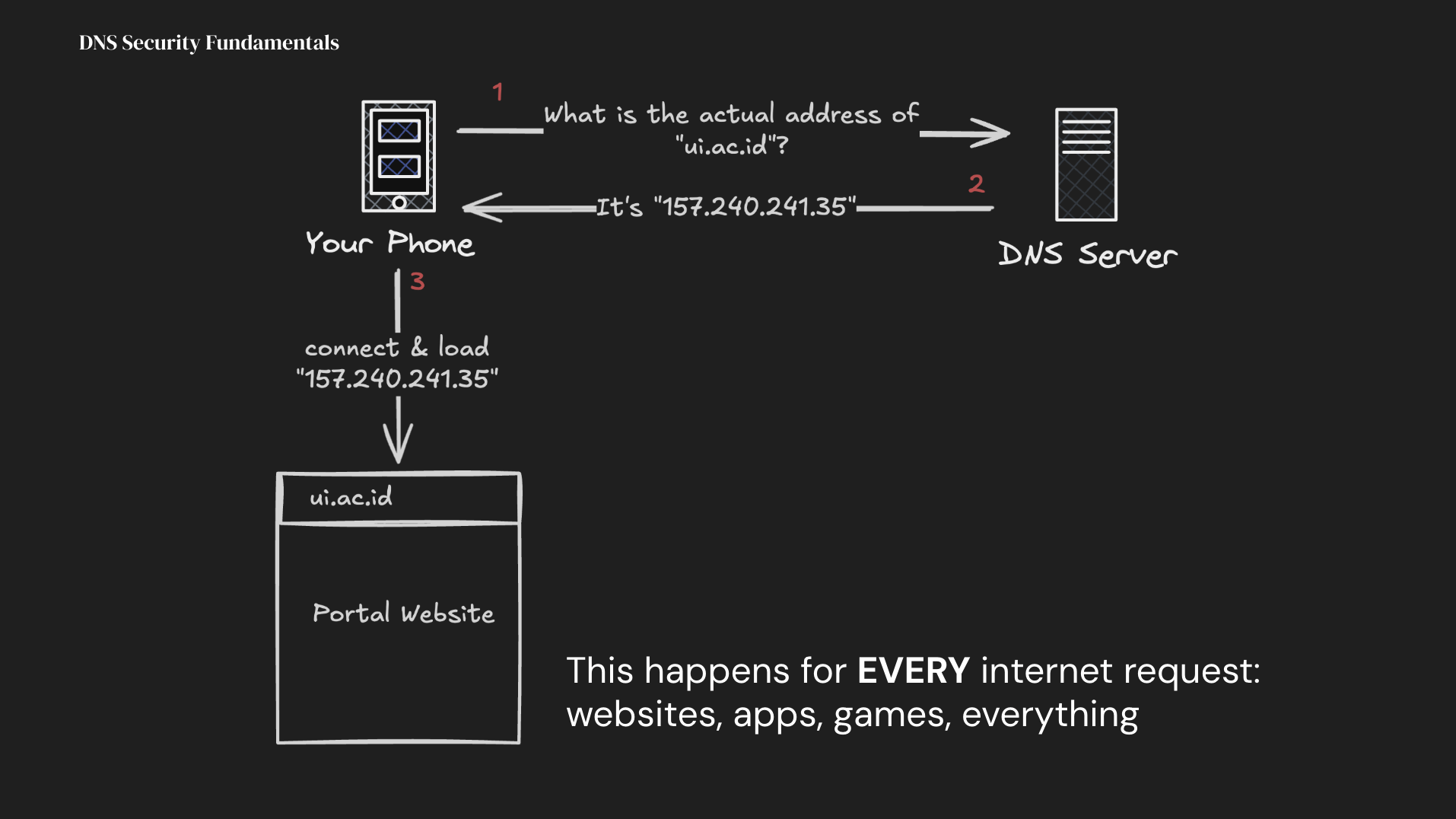
What DNS actually does? Just like you need to look up someone's number before calling them, your device needs to "look up" a website's actual address before connecting. And, this happens for EVERY internet requests you did (or, your device did without you knowing), for every websites, apps, games, basically everything. Which, this means one compromised DNS setting CAN AFFECTS everything.
Let's take a look on real attack scenario: The Banking Trap App
Normally, when user open banking app (let say) BCA → DNS lookup for "bca.co.id" → Gets real IP: 159.53.224.1 → Connects to real BCA server.
But, when you connect your device with unsecured access point (e.g. Public WiFi), you open BCA app → DNS lookup intercepted by attacker → Gets fake IP: 192.168.1.100 → Connects to fake BCA site 💀 → you enter password → Attacker steal your credential 😨.
And, the scary part is: You see no difference, the fake BCA site looks identical to the real one.
This is why, it doesn't matter what platform you are using, you still need to be aware and of course, we also want to protect you :)
How we protect you?
We build a mobile app that changes how your device handles DNS queries, allowing you to use our DNS servers and providing additional features like encryption, ad blocking and privacy protection.

DNS over HTTPS (DoH) on iOS
For the encryption, we use DNS over HTTPS (DoH) which it encrypts DNS queries by wrapping them in HTTPS traffic on port 443, making them indistinguishable from regular web traffic.
Apple announced support for DNS over HTTPS (DoH) starting with iOS 14. They also give users more control over DNS settings. Before iOS 14, DNS queries were generally sent over plain text. (Source: WWDC 2020, Encrypted DNS).
The research of DoH
I would say developing a DoH application for iOS isn't easy. Even though Apple supports developers with a public API, the documentation for it is like searching for a needle in a haystack.
We found that there are two ways to create and manage system-wide DNS configuration on iOS device, one way is using an MDM (Mobile Device Management) to configure enterprise settings on the device. Another way (which we will dive more into) is using NetworkExtension.
First thing first, you need to add the Network Extension entitlement. You can do so by navigating through:
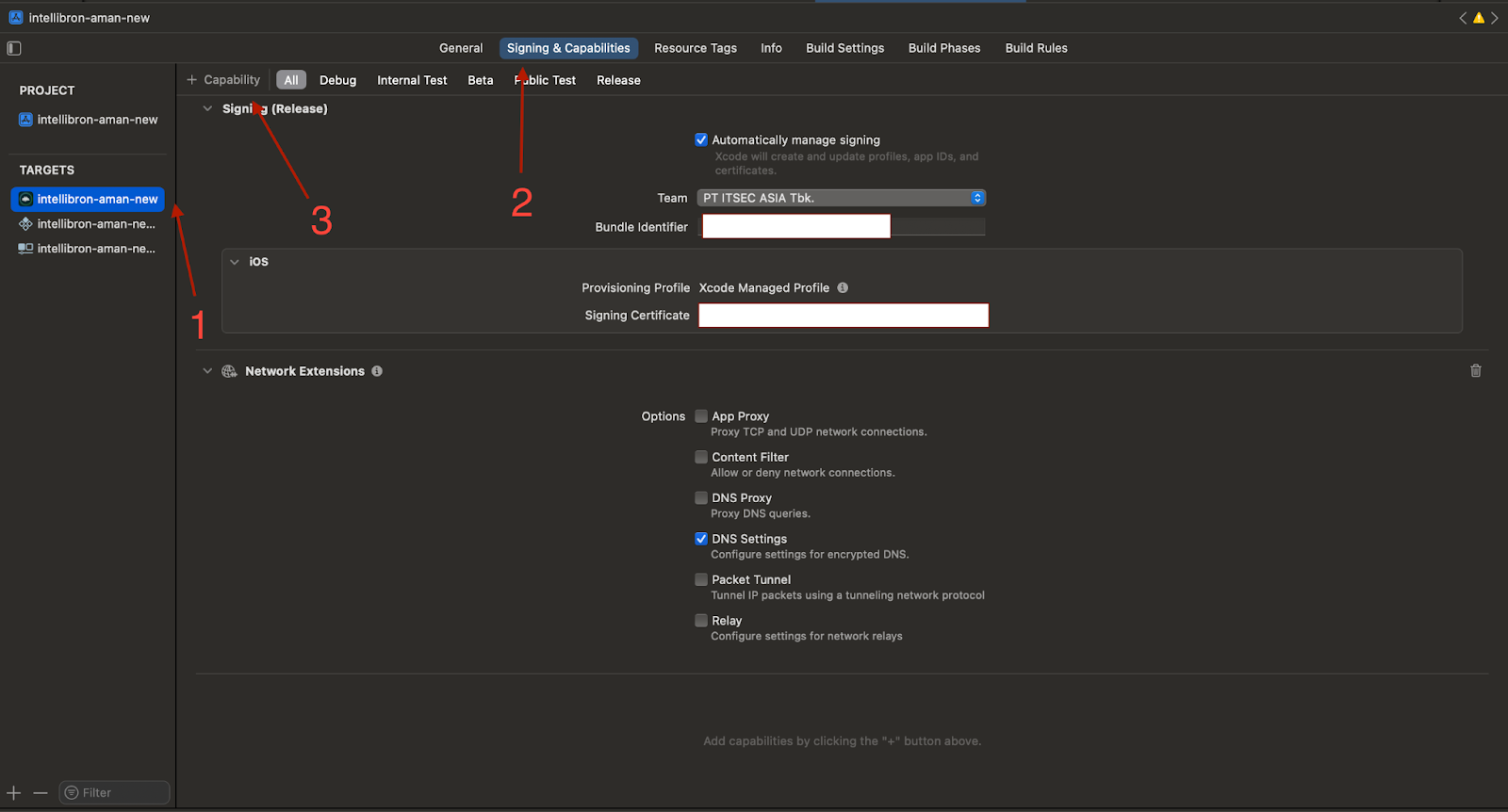
- Xcode by navigating to the target
- Go to "Signing & Capabilities"
- Press the "+ Capability" button
- Look for "Network Extensions"
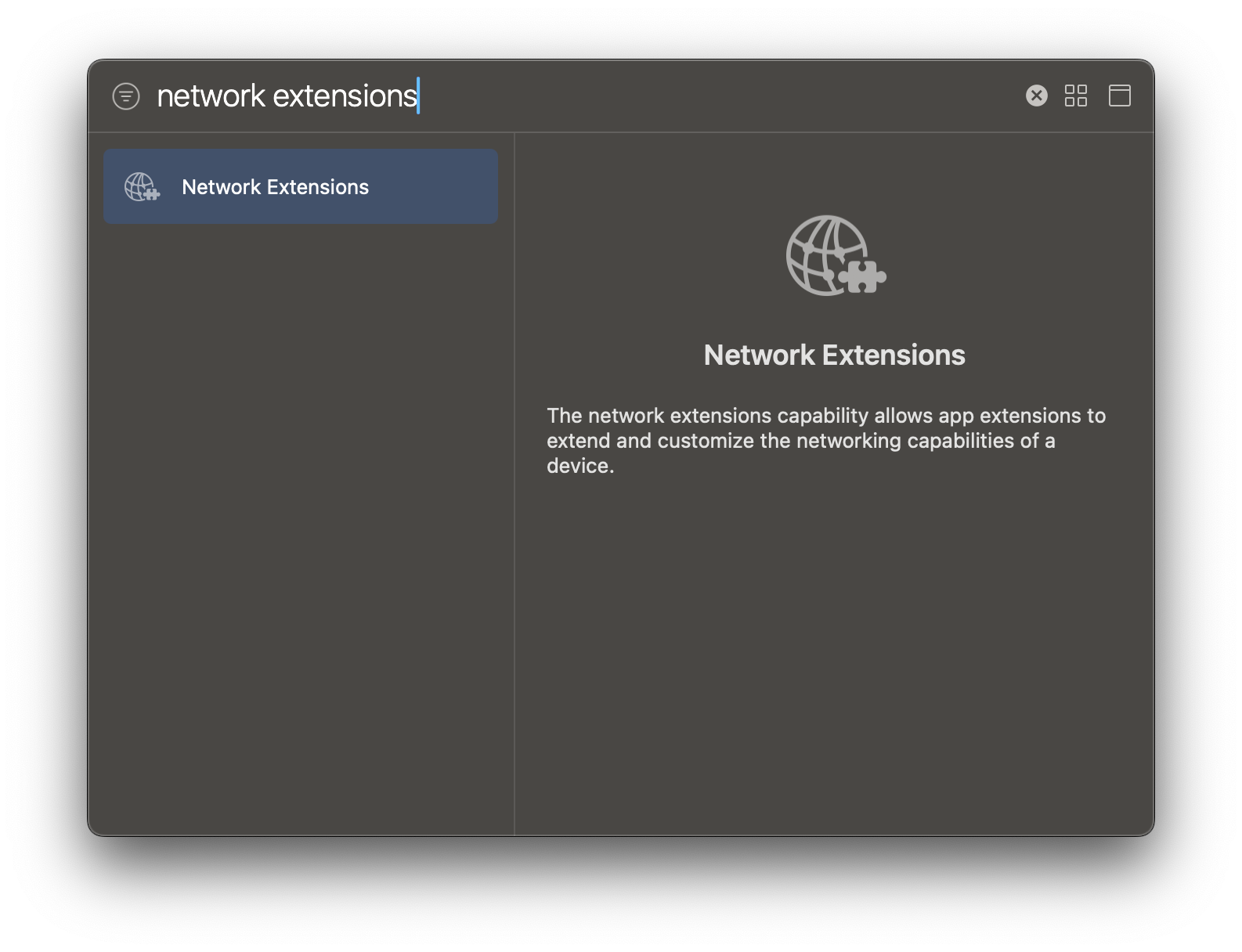
- After that, check the "DNS Settings" option from the Network Extensions capability
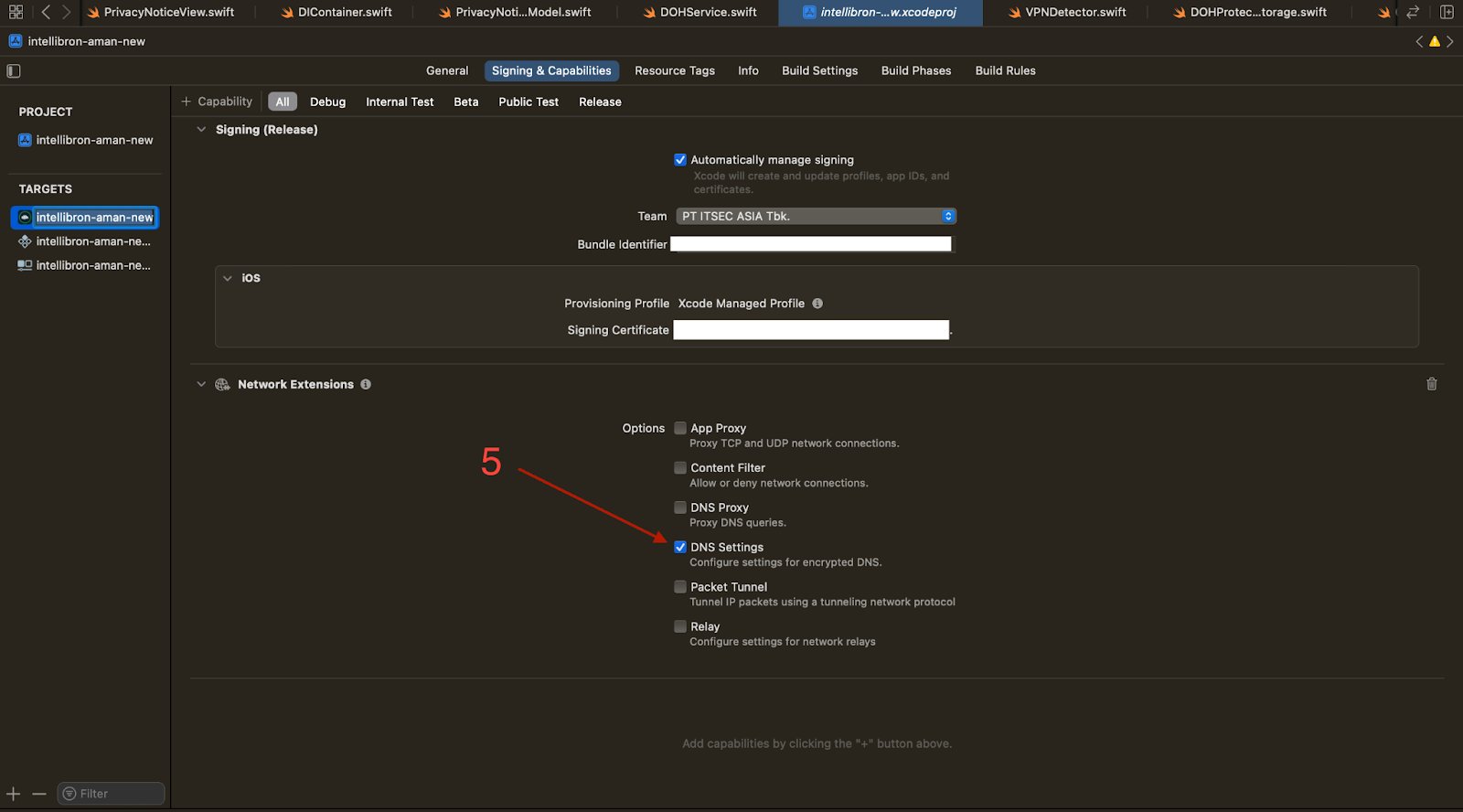
Setting up is done, now you are ready to code 👨💻
Code, code, code
We will do this by create a class called DOHService. This class will be handling all DoH related functions which are: setting up, turning on/off, and check whether the user using DNS configured by our app or not.
Basically, we can just finish here. But, to really turning on/off the DNS configuration via our app we are utilizing the on-demand rules (NEOnDemandRuleDisconnect) that we mentioned above.
So, when the user wants to turn off, we can just disconnect all types (WiFi & Cellular) of connection, and when the user wants to turn it on, we can just reconnect to all types of connection again.
And, to check if the user has already selected our DNS configuration by:
Well, that's it. Now, we have our own DoH service 🕶️
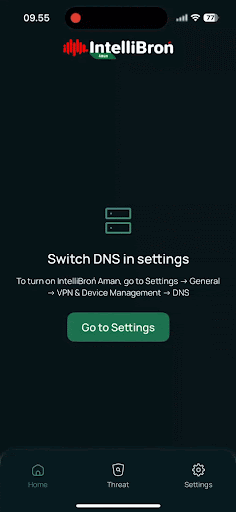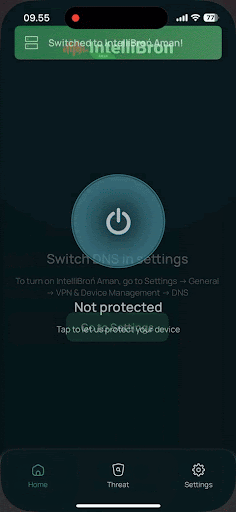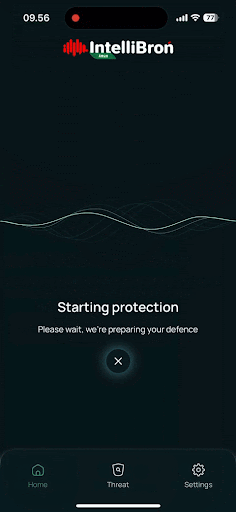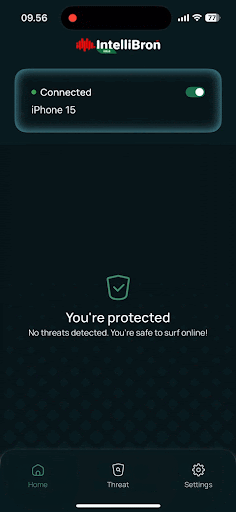
Our mindset when we are building this app, this isn't just about writing code, but about creating a shield for users who unknowingly expose themselves to DNS-based attacks. Every time someone connects to public WiFi at a coffee shop, airport, or hotel, they're potentially one malicious DNS redirect away from losing their credential or personal data.
What we've built here represents more than a technical solution; it's a step toward democratizing cybersecurity. By implementing DNS over HTTPS at the mobile application level, we're putting enterprise-grade protection directly into users' pockets. The beauty lies in its simplicity–users don't need to understand the technical complexities of DNS poisoning or man-in-the-middle attacks. They just need to install the app and stay protected.
To fellow developers, I would say in this era the real challenge isn't coding but is to understand that you are not just building an app, but also building trust. Every user who uses your app is placing their trust in your hands.
Lastly, stay curious, stay secure and catch you on the next one! 😼



